Earlier, I’ve already published information about the critical vulnerabilities and backdoors in D-Link DIR-620 (RevG), that I’ve discovered and submitted to the vendor. The D-Link DIR-620 routers is a model of router, that popular in Russia and CIS countries (most home routers are located behind their ISP’s NAT, which is why these routers don’t appear in the statistics) due to one of the ISPs delivered to its customers (this conclusion is based on the fact that the router is provided as part of the standard customer contract and the hardcoded credentials contain the name of the ISP in the login string).
Note: the following information about vulnerabilities has been submitted to the respective stakeholders (D-Link, ISP provider, Mitre) and we are publishing this information in accordance with vulnerability disclosure policy.
The following advisory describes four vulnerabilities and hardcoded accounts in D-Link DIR-620 firmware (RevG). The impact of vulnerabilities described in the previous advisory. Here we want to publish information about new critical issues, that were identified in firmware version 1.0.37. Based on the information we will propose recommendation, how to mitigate the vulnerabilities.
Technical details
Sensitive data exposure in config-file (CVE-2018–12677)
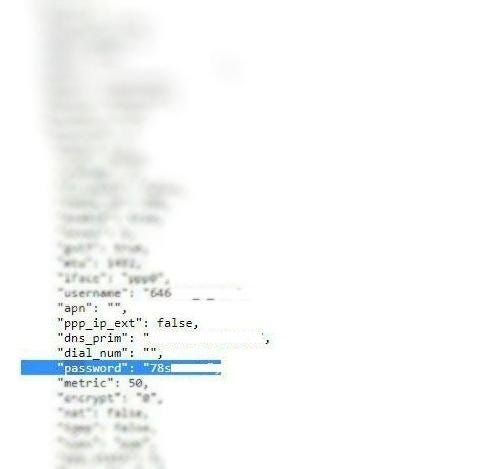
Using the code-injection vulnerability (OS command injection, CVE-2018–6211) attacker can extract a config-file “tmp/config.json” with all user’s credentials inside in plaintext.
Vulnerability metrics:
CVSS Base Score: 7.5
Vector: (AV:L/AC:H/PR:H/UI:N/S:C/C:H/I:H/A:H)
Sensitive data exposure for unauthenticated user (CVE-2018–12419)
Vulnerability CVE-2018–12677 exposes all user credentials in config-file (plaintext) inside the firmware. Part of the file is stored in JavaScript variable, that available for unauthenticated user in the web dashboard. It contains sensitive information (for example, user’s password for their Internet connection).

Vulnerability metrics:
CVSS v3 Base Score: 7.5
Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N)
Hardcoded credentials for web dashboard (CVE-2018–12676)
As I mentioned before, CVE-2018–12677 exposures a config-file in plaintext. I found there the strange account with following login name: “support<substring>”. It turned out, the credentials for web dashboard are hardcoded for ISP support purposes (according to the Vendor’s statement). Using the account, an attacker can gain privileged access to the router’s dashboard.

Vulnerability metrics:
CVSS v3 Base Score: 10.0
Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H)
How to fix it
To fix the vulnerabilities, the user needs to update their firmware to the latest version (2.0.22). Despite the fact that vulnerability CVE-2018–12677 will not be fixed, sensitive data exposure for the unauthenticated user (CVE-2018–12419) will be fixed. However, we identified that after the update procedure, part of the config-file migrates to an updated version as a legacy part. As a result, backdoor credentials still exist. That’s why I recommend performing the following steps:
- Update firmware to the latest version (2.0.22)
- Restore router’s settings to factory settings
- Restrict any access to the web dashboard using a whitelist of trusted IPs
- Restrict any access to Telnet
- Regularly change your router admin username and password
Advisory Status
01/15/2018 — reported to vendor
01/15/2018 — reported to ISP
01/24/2018 — received a response from ISP
02/06/2018 — received a response from vendor. Official statement: the devices were not intended for retail and were delivered to customers through a ISP who requested customization.