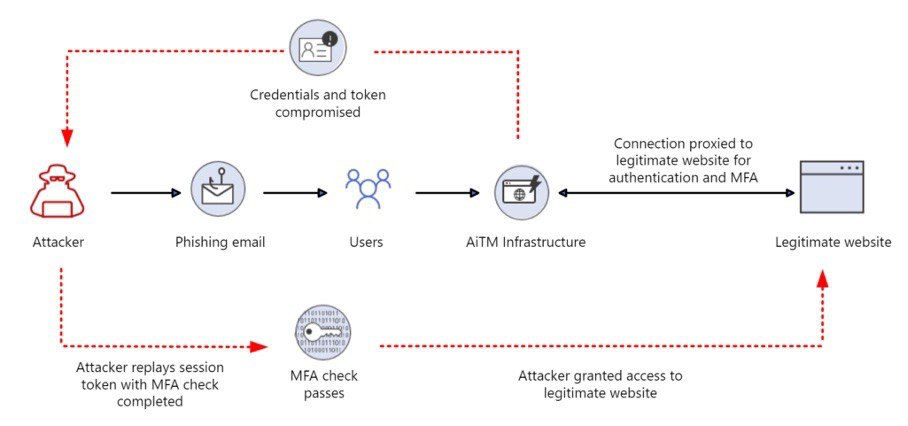
Типичный сценарий социотехнического пентеста: собрал список корпоративных email-адресов, настроил инструмент для проведения фишинговых рассылок, провел рассылку, получил учетные данные сотрудников для доступа в корпоративную инфраструктуру.
After completing the MBA programme, I had opportunity to spend additional semester focusing on advanced management disciplines and preparing my master’s thesis. This stage was primarily dedicated to research, with many ideas grounded in academic papers.
Back in 2015, I had my first international talk at Nullcon in India. Warm community, great people. I left with Indian friends and strong impression.
Five years later, BSides Cairo became my first experience on the other side of the table — joining the Advisory Board.
Now the paths cross again: I’m joining BSides Vizag as an Advisory Board member to help bring best-in-class research to the stage.
CFP is open. Submit your research and let’s make it big.