Let’s talk about last year’s perspective research. Researchers have gathered a wealth of interesting material. Let’s go through the reports to see what can be applied in practice and what is worth deeper exploration.
Attacking the developer: vulnerability in WinDBG
Let me start with some research conducted by our Advanced Research Team. We discovered an interesting feature in WinDbg, a standard Windows debugging tool. This flaw allows malicious code to be executed on a developer’s host and enables the replacement of libraries.
A lesser-known fact is that the PDB debugging symbol format provides not only code symbols and structures but also information about the location of the corresponding source code. This mechanism, known as SrcSrv, can be exploited through incorrect configuration. An attacker could override the path to WinDbg extensions, enabling a DLL hijacking attack that links arbitrary DLLs, including those hosted on a remote SMB server.
Attack surface:
- The vulnerability affects environments used by developers or analysts working on Windows applications.
- WinDbg does not update automatically, requiring manual updates—making the patching process more complex.
- Potential consequences: Intellectual property theft or source code compromise of in-development software.
Microsoft has confirmed the vulnerability and has prepared a patch for WinDbg 10.0.22621.0 and higher and Windows SDK 11. The report is available in English. We have also developed tool that checks dump files for references to PDB files.
Attacking the Developer: repojacking research
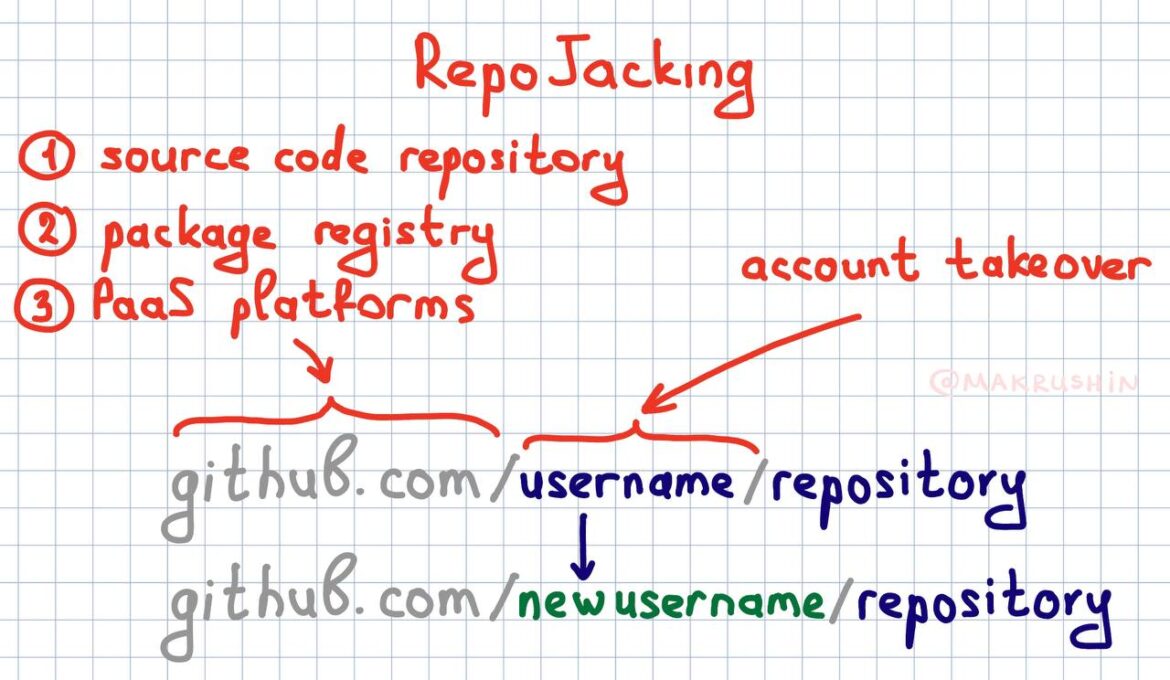
Repojacking, or repository hijacking, is an attack method that allows an attacker to gain full control of a repository’s source code. This enables the attacker to execute arbitrary code within any context linked to the compromised repository.
If a developer integrates third-party code from a repository and the owner of that repository later deletes, moves, or sells their account, a malicious actor can re-register the account. They can then inject malicious code into the repository, compromising all applications that depend on it.
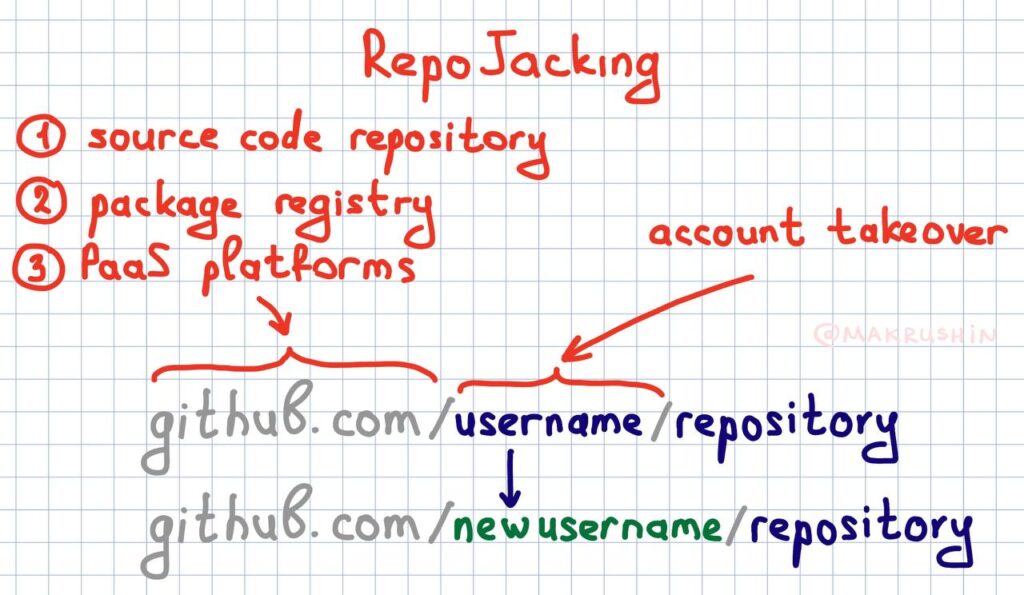
Here’s how ART tackled the issue:
- Extracted all GitHub references from dependency code in the two most widely used package managers for Python and JavaScript: PyPI and NPM.
- Removed duplicates and checked the availability of all links, flagging those that returned a 404 error as corrupted_links.
- Examined all corrupted_links for potential account takeover attacks.
As a result, we generated statistics on vulnerable GitHub repositories that attackers could already exploit to spread malicious code through the supply chain. We’ve published the full results of this research, along with our methodology and tools.
Method of finding n-day vulnerabilities in binary code
Fuzzing has long been an effective method for identifying software bugs, and I enjoy using it occasionally. By targeting less popular applications and running tests, you can uncover numerous vulnerabilities within a week.
In addition to traditional methods, a new approach deserves attention: BinGo: Identifying Security Patches in Binary Code with Graph Representation Learning. This method identifies security patches in application binaries, which is particularly useful when developers secretly patch vulnerabilities without logging them as CVEs or mentioning them in changelogs.
The method represents a binary file as a Code Property Graph (CPG), an intermediate representation of code designed for security analysis. The CPG includes an abstract syntax tree, control flow graph, and data dependencies.
What makes this method unique is its ability to compare binaries before and after changes using a Siamese neural network. This network identifies similarities and differences, with a detection accuracy of 80.77% for security patches among other binary changes. What sets it apart is a new model for detecting security patches that compares binaries before and after changes.
Idea: could this approach detect deliberately placed backdoors in binary code? Here’s how to test this hypothesis:
- Identify examples of code changes that serve as backdoors.
- Generate CFGs (Control Flow Graphs) for these examples.
- Train a Siamese network to detect similarities between CFGs and the target CFG.
You may have read my article ‘How to do your first security research‘. I think testing the above hypothesis would be a great topic for such a study!
Finding secrets in video content
We’ve long known how to identify secrets like passwords, tokens, and API keys in source code. Now, GitLab researchers have developed a method to find secrets in video content.
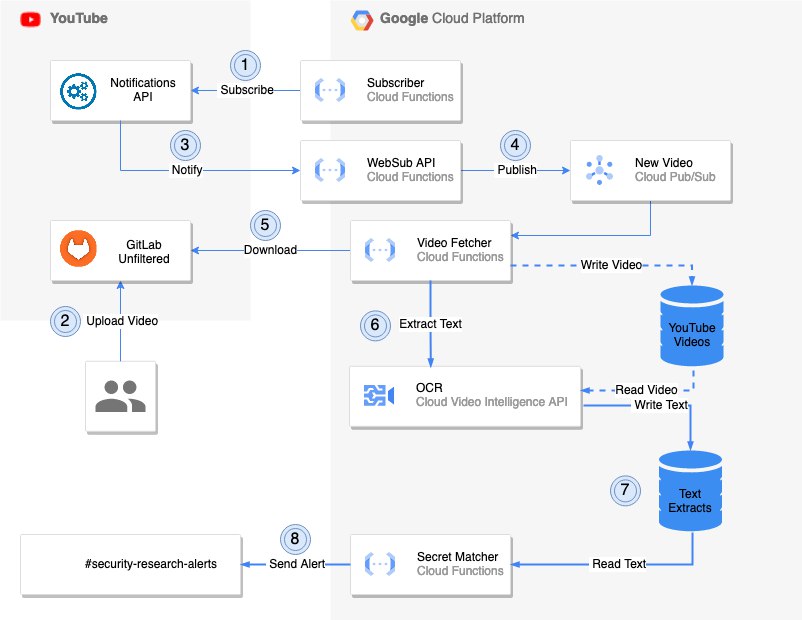
The tool splits videos into individual frames, extracts text using OCR, and analyzes the text for specific patterns. It’s designed to identify sensitive information in work meetings and monitor publicly shared content on social networks and video platforms.
Morris II: the first malware targeting generative AI
The research behind the sensationally named “Morris II” attack explores vulnerabilities in generative AI systems that can be exploited for malicious purposes. While the name may be hype-driven, the concept deserves attention.
Researchers demonstrated how malicious queries can provoke an ML model into replicating harmful input. The model then performs an unintended malicious action, targeting other components in its ecosystem.
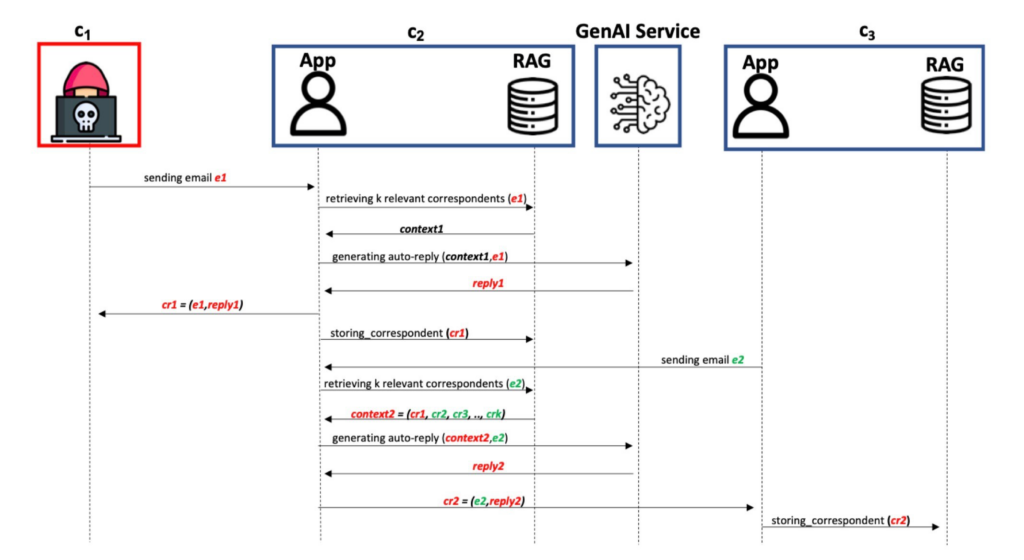
The attack takes place without user intervention, but I still wouldn’t call this futuristic malware a worm. It’s more like an SSRF: you can manipulate the components of the ecosystem in which the vulnerable model resides. But for it to be a real worm, you probably need the model to start sending requests outside its ecosystem to other similar ML models.
So the concept of attacking products is interesting, but I think the comparison with Morris is a bit misplaced. Neither in the way it works nor in its potential destructiveness.
Secure by design: Google’s principles for building secure systems
Last year, while researchers uncovered a hidden backdoor in new versions of the liblzma library, I was exploring Google’s Secure by Design principles. These principles focus on user-centered security and building systems that enforce invariants — properties of a system that remain unchanged regardless of user actions or attacks.
The purpose of this document is to bridge the gap between the conceptual requirements of Secure by Design and its practical application. Google engineers faced a significant challenge: the rapid pace of change in software development, particularly in cloud software, which often involves several releases per day. This pace makes it difficult to implement existing security requirements, which were initially designed with physical systems in mind. In physical systems, careful architectural design minimizes the risk of failure during the production phase, whereas in software, the risk of failure increases with frequent updates.
User-centred design is perhaps the most important requirement. In practice, this means designing a product’s security requirements and architecture around the actions of its users. For each action, you need to assess how it could lead to undesirable consequences. At the same time, the developer is also a user.
Another key concept is design thinking in terms of invariants. An invariant is a property of a system that remains constant, regardless of the actions taken by its users or attackers. In the context of security, an invariant represents a stable system state. For example, all network traffic passing through unsecured channels must always be protected by a secure protocol.
Security invariants help to eliminate user requirements and focus the design on the requirements of the system the user is working with. The implementation of all invariants can be automatically checked at the software quality analysis stage.
Incidentally, the concept of immutable infrastructure was once introduced, and now invariants allow the architect to implement the same principles at the development stage.
Threat detection strategy: where should we focus our efforts in developing detection methods?
How can we effectively detect threats with limited resources? How do we evaluate the quality of detection methods? I have come across several articles where authors explore answers to these questions.
Security engineers and SOC analysts understand that a key objective in threat detection is to build mechanisms capable of identifying and preventing as many methods as possible that an attacker might use to progress. Achieving this goal presents a significant challenge: stopping an attacker from completing their entire sequence of actions while remaining undetected. This is where probability comes into play: how likely is it that an attacker will choose a path the defender fails to detect?
The following model provides valuable insights:
- We represent each technique in the MITRE ATT&CK matrix as a single point.
- The attacker’s progression, from gaining initial access to advancing toward their target, can be mapped as a specific sequence of points.
- Matrix techniques that include multiple sub-techniques can be broken down into groups of points. The larger the group, the higher the probability of successfully applying a particular technique.
- Each sub-technique can be executed using various procedures and tools, which further increase the number of points within the groups.
- Detection Tactics: The effectiveness of a detection method is determined by the number of procedures it covers within a sub-technique. A highly effective method detects the procedure with the most connections to other procedures.
Here is a hypothesis that can be tested in a research paper: create a graph of all MITRE ATT&CK procedures and identify the nodes with the highest number of connections (the example in the figure is highlighted in yellow).
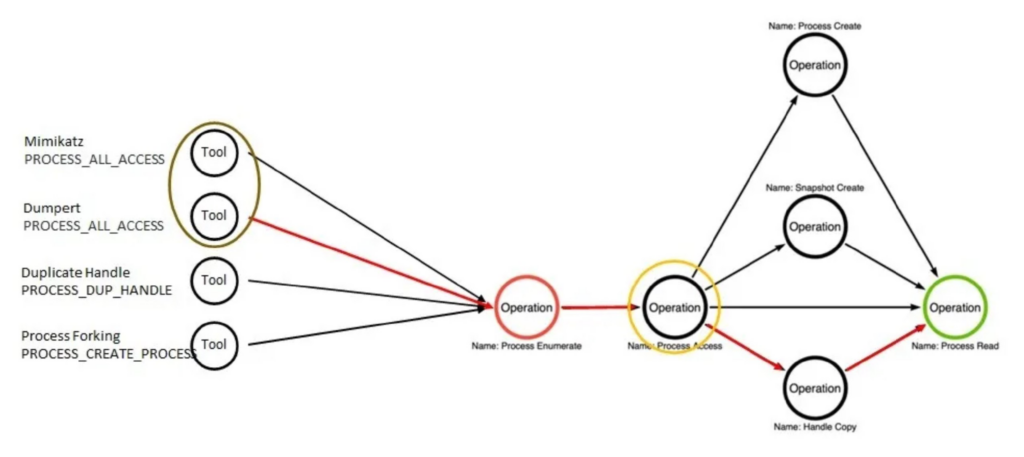
These nodes can serve as the foundation for building a defense system and will help prioritize efforts when resources are limited. Analysts in the monitoring center will gain a quantitative method for justifying the development of new detectors or the purchase of the “right” protection tools.
Analysis of zero-day vulnerabilities used in attacks over the past year
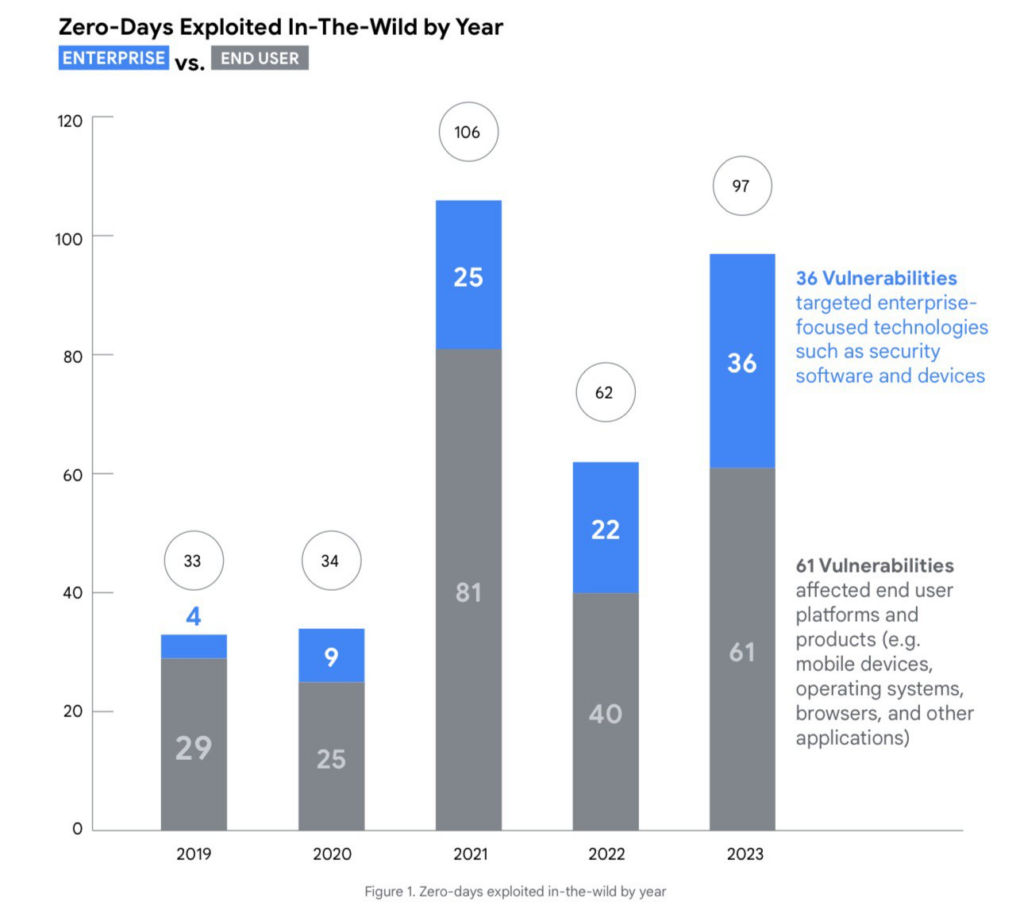
Google researchers have published a report analyzing zero-day vulnerabilities exploited in 2023.
Interesting facts:
- A total of 92 vulnerabilities were analyzed, 61 of which were found in consumer products and platforms, while the remaining vulnerabilities were in enterprise software. Attacker interest in user data remains consistent.
- Attackers are increasingly focusing on compromising third-party components and libraries. The trend of supply chain attacks continues to grow (I’ve shared more on this topic in my channel).
- The proportion of zero-day attacks used for financial gain is declining. This shift can be attributed to the fact that using expensive exploitation tools for such attacks is no longer economically viable. Instead, attackers are opting for cheaper alternatives that yield similar results.
Increasing the level of observability for DevSecOps
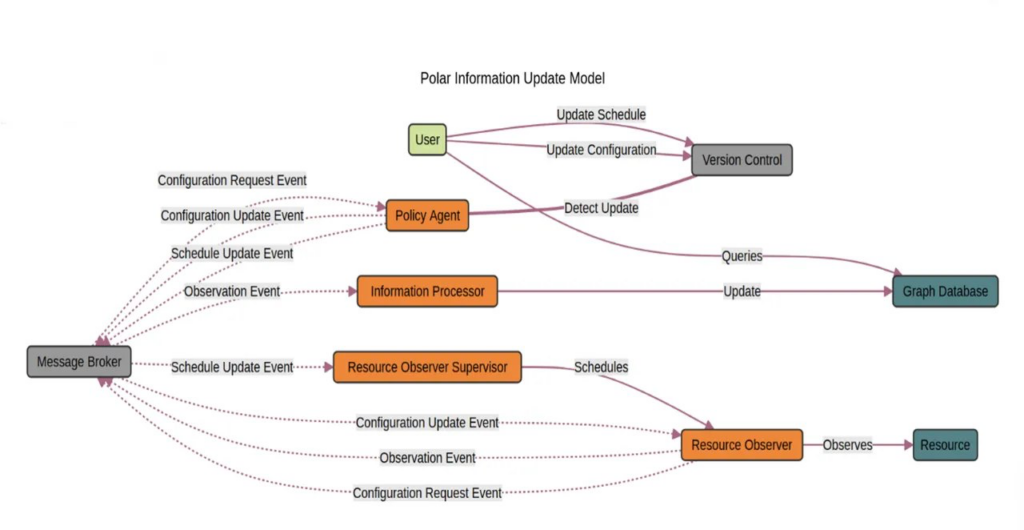
Carnegie Mellon University has released the Polar framework, which enhances the observability of data within software development platforms. The primary objective is to improve the speed and quality of decision-making in DevSecOps pipelines.
At the core of the framework’s architecture is a graph database that manages data and represents it as a graph. This graph captures the relationships between different roles involved in handling data:
- Observers — components responsible for monitoring resources and environments.
- Information Processors — elements that transform raw data from observers into structured data stored in the graph database.
- Policy Agents — components that control all system elements, ensuring they operate within defined parameters through configurations.
A graph serves as a data model that reveals the real relationships in an organization’s operational activities. I suggest a potential use case: analyzing existing DevSecOps processes to optimize workflows and reduce time-to-deploy.
Vulnerabilities on GitHub: in Ruby library downloaded 250,000 times, modules for electronic locks, and popular game extensions
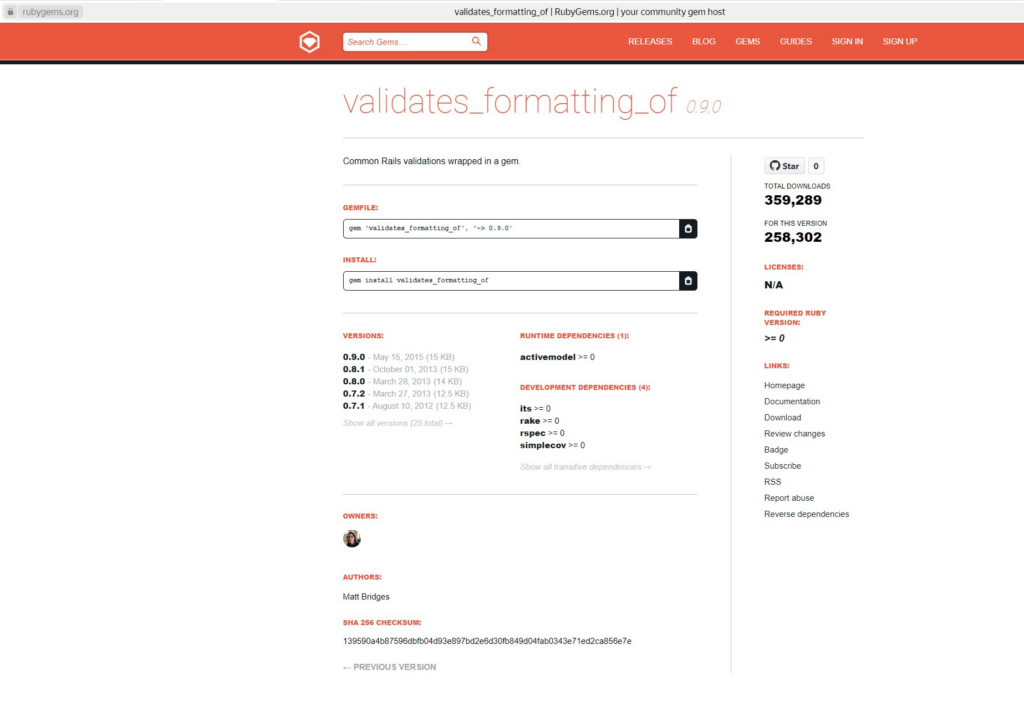
As part of our research, we analyzed public GitHub repositories for RepoJacking vulnerabilities. We then went a step further and examined popular libraries among these repositories. We focused on repositories containing code published as libraries in package managers. These repositories were scanned for vulnerabilities, and we identified the most popular ones. Here’s what we found:
- Ruby library, the latest version of which has been downloaded over 250,000 times, along with other Ruby modules published on RubyGems.
- Python module used for controlling electronic door locks manufactured by a well-known company.
- Modules for popular games, including Counter-Strike and Minecraft.
- An extension module for the Godot engine.
- Container images published on Docker Hub.
Recommendations for developers have been prepared, and the results of the study have been published.
Selection of research topics from Black Hat 2024
The biggest cybersecurity events took place in August, and reviews of the most high-profile studies from a media perspective are already available.
I have reviewed the material and highlighted some promising trends.
- From Weapon to Target: Quantum Computer Paradox. This study explores the security challenges of quantum computers and the quantum computing process. While the impact of quantum computing on classical cryptography is widely discussed, the security of quantum systems themselves remains poorly understood. The authors analyze vulnerabilities and potential attack vectors in quantum computing infrastructures, including software and cloud services. Examples of identified issues include theft of authentication tokens, manipulation of quantum software chains in SDKs, and attacks on quantum processors.
- SnailLoad: Anyone on the Internet Can Learn What You’re Doing. This fascinating technique profiles a user without using any supporting tools (e.g., agents on the workstation or proxies on the network). The data leakage channel lies in the network delays caused when a user interacts with online content. By analyzing these delays, an attacker can infer the user’s actions, potentially disclosing sensitive information and compromising anonymity. This technique demonstrates the vulnerability of even secure browser sessions to advanced timing attacks.
- Listen to the whispers: Web Timing Attacks that Actually Work. This study expands on timing attacks, specifically in the context of web application security. It provides examples of scenarios where a system unintentionally leaks sensitive data through timing variations in request processing. The technique is valuable for identifying hidden attack surfaces and detecting misconfigured proxy servers.
- Deep Backdoors in Deep Reinforcement Learning Agents. This research presents a technique for embedding ‘malicious neurons’ into a neural network. It describes scenarios where AI agents are compromised during their training phase, leading to potentially harmful decisions in critical areas such as industry, autonomous transport, and cybersecurity.
Technology announcements from RSA Conference 2024
Announcements from RSA this year that caught my interest:
- ArmorCode, a provider of Application Security Posture Management (ASPM) solutions, has integrated AI into its platform to correlate vulnerabilities and accelerate remediation.
- Checkmarx released AI security capabilities to protect code generated with LLM. It has also added auto-patching capabilities for vulnerabilities.
- The Cloud Security Alliance has published guidelines for the secure use of AI. It has published three key documents that CIOs and AI leaders should review: AI Organisational Responsibilities, AI Resilience and Principles to Practice.
- Protect AI has launched an AI/ML vulnerability database. The company highlights that existing CVE and NVD databases do not adequately cover vulnerabilities in machine learning models and AI-related issues.
- Startup Torq has released HyperSOC, a solution powered by LLM analytics to automate the assessment of threat criticality and determine the best response and escalation path. An unusual selling point of this technology is its promise to “eliminate SOC specialist burnout.”
Perspective tools: PyPI and NPM malicious dependency discovery
In my earlier discussion about attacks on the development pipeline, a common question from developers was: what tool can I use to analyze the dependencies in my code?
GuardDog is a tool that utilizes Semgrep to scan PyPI and NPM packages for malicious code. Its heuristics database is divided into two categories: source code heuristics and package metadata heuristics. Using this tool, DataDog’s research team recently discovered several malicious PyPI packages targeting certain macOS workstations.
This tool can be adopted to continuously scan local package repositories and enhance supply chain security.
Perspective tools: password list with most popular passwords
The file rockyou2024.txt contains 9.94 billion unique passwords, many of which originate from major data breaches. Who might benefit from this file:
- Red Teamers, Pentesters, and Security Analysts. Regularly updating password lists is crucial for password mining. Even the older rockyou.txt from Kali Linux proved effective on a large scale during penetration tests.
- Defenders, SOC Analysts, and Security Engineers. They can use the file to evaluate password policies for brute-force resistance and integrate popular password combinations into detection rules to identify attacks.
- Ordinary Users. They can search for their own passwords in the file, offering another compelling reason to update their credentials.
Perspective tools: what can a shadow in a photo tell you?
The answer is: location.
For OSINT researchers, I recommend a useful tool called ShadowFinder. This tool helps determine the approximate coordinates of where a photo was taken. It works by analyzing the height of an object, the length of its shadow, the date, and the time, then estimates locations where a shadow with these parameters could exist.
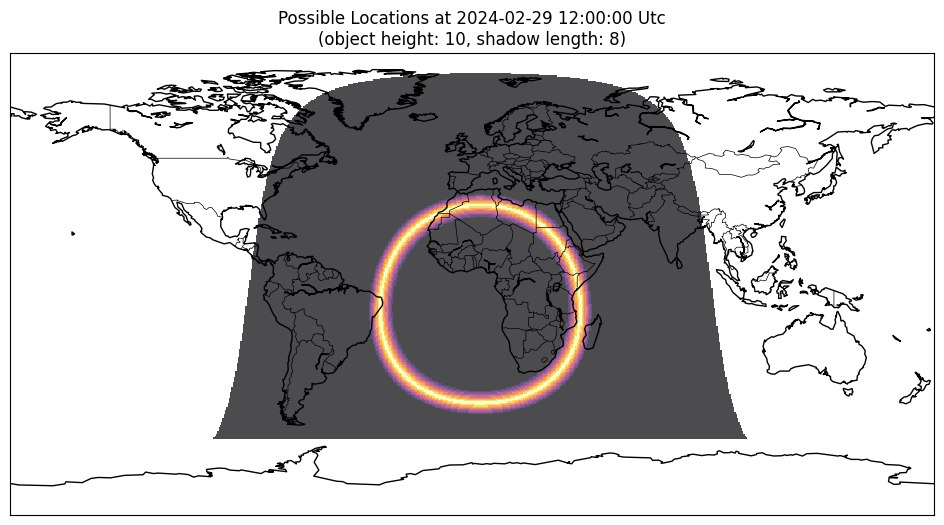
If you want to avoid revealing your location, consider blurring shadows in your photos—or stop posting photos altogether—because detection is highly effective.
Critical vulnerability in Windows network stack
A critical vulnerability has been identified in the Windows kernel IPv6 parser. This flaw allows an attacker to remotely execute arbitrary code without requiring user interaction.
Notably, a local firewall won’t help in this case because the malicious IPv6 packet is processed before it reaches built-in defenses. All supported Windows versions are affected. Make sure to install the latest updates and prepare for potential exploits.
Conclusion
As we look ahead to 2025, the lessons and insights gained from these research findings serve as invaluable tools for navigating an increasingly complex cybersecurity landscape. Whether it’s understanding new attack surfaces, enhancing observability, or adopting innovative tools, the key to effective cybersecurity lies in combining research-driven approaches with practical application.
Use this experience and knowledge to refine your strategies, strengthen your defenses, and take your findings forward in 2025.