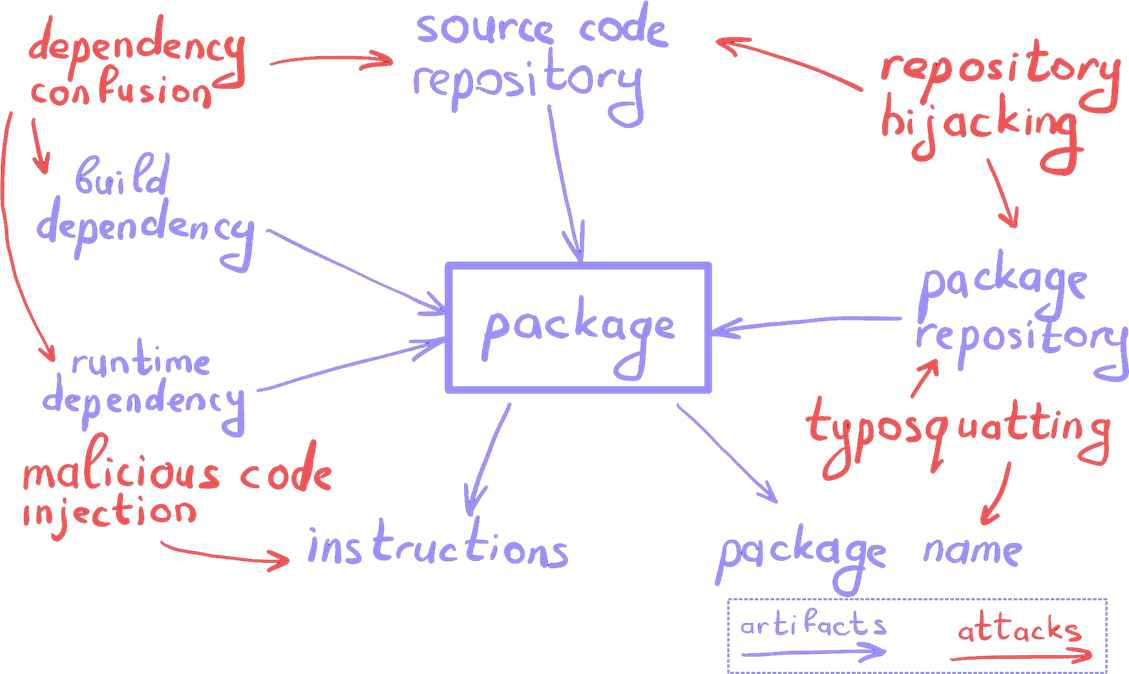
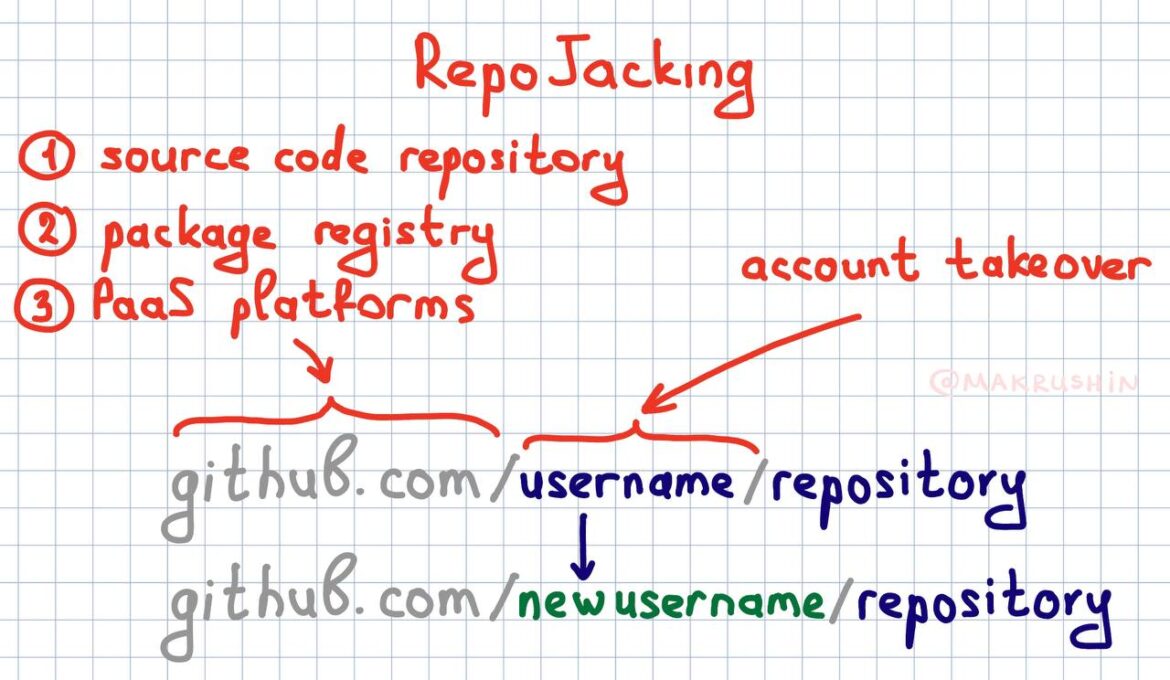
In 2024, GitLab developers discovered two critical vulnerabilities in their system. Due to verification errors, attackers could hijack user accounts and modify repository contents. This type of attack is known as RepoJacking.
We conducted a comprehensive analysis of GitHub, another major code hosting platform, and identified 1,300 vulnerable open repositories. What are the implications for developers and their projects? Let’s explore.