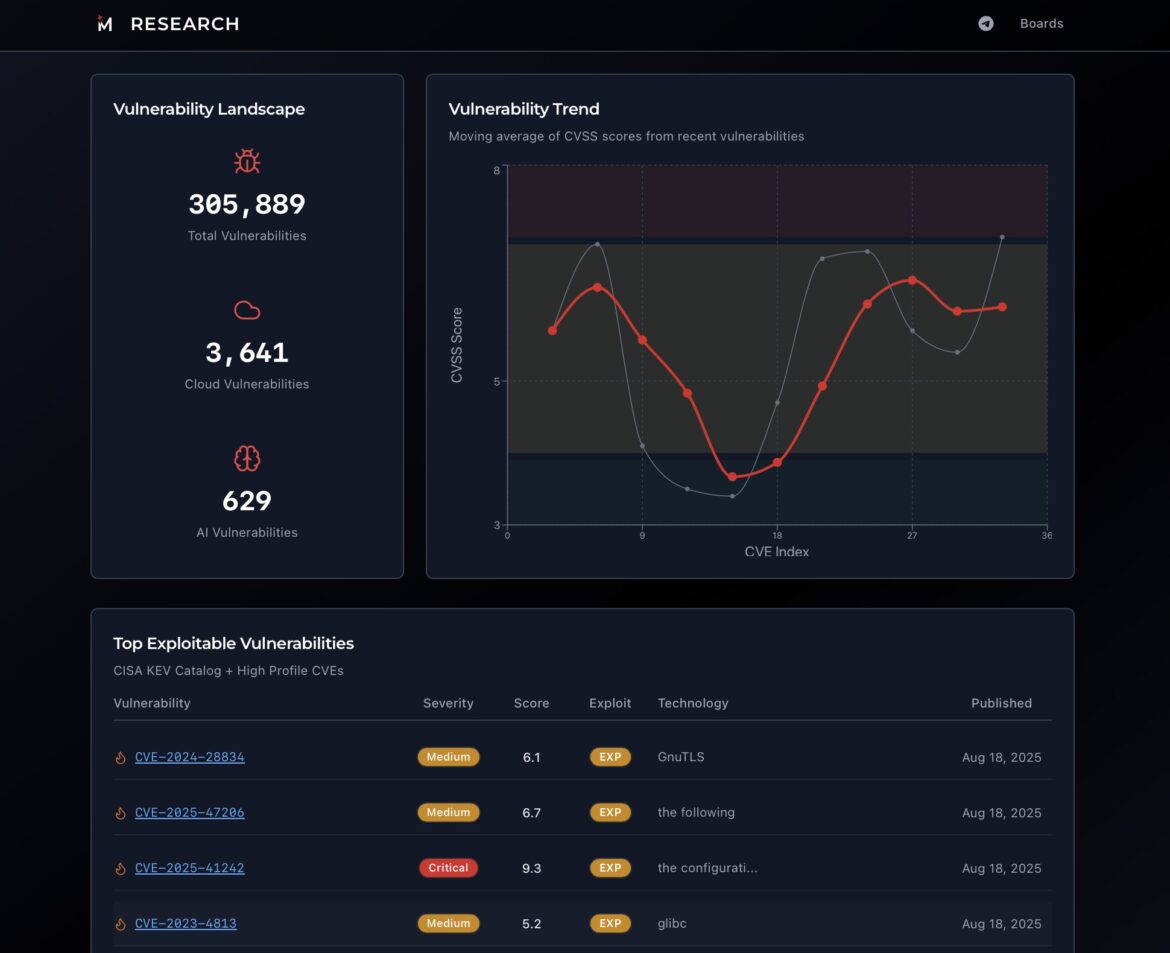
As long as the CVE remains the main index of known vulnerabilities, teams of security analysts and engineers will develop processes to track updates. They will not only track changes, but also enrich database with additional data to help them prioritise fixes accurately.
vulnerability assessment

Payment systems are a tidbit for an attacker, but often it’s non-achievable scope for bug hunters outside the company. Bug bounty programs of financial organizations include resources that are on the surface of the attack, and it’s quite difficult for a researcher to dig deeper into the internal financial processes. So we have to limit ourselves with XSS, SSRF in a web-application of the payment system.

Quick summary of Bug Hunting Village, the first time we organized offline:
- 12 talks and workshops focused on vulnerability research and bug bounty;
- highest payouts during two days of conference by our partners (thanks to Mail.ru Group, VK.com, Азбука Вкуса, Avito, iSimpleLab);
- prizes for most active bug hunters (thanks to PHDays organizers and Timur Yunusov);
- communication in our Chat and knowledge sharing in Telegram-channel, and continuous movement to the next offline event.
Красная команда имитирует действия атакующего, чтобы помочь оценить эффективность защитных мер и улучшить безопасность. В этой статье я разберу, как устроены такие команды и какие нужны области экспертизы для успешной реализации kill chain и демонстрации результатов.
В прошлый раз мы познакомились с ключевыми целями и показателями эффективности Red Team для процессов ИБ и бизнеса в целом. Мы рассмотрели особенности взаимодействия экспертов наступательной безопасности c Blue Team, нюансы ведения проектов и коммуникации во время работ. При этом мы практически не коснулись внутренней структуры красной команды. Пора исправить это!

Are you planning to get into application security, but don’t know where to start? Today at #TheSASonline workshop I will introduce the fundamentals of web-applications vulnerability research. We will start from the basic, but important techniques to gradually build-up to the level where attendees can not only use the tactics, techniques, and tools to assess various components involved in bug hunting but also walk away with a solid understanding of the concepts on which these tools work. And you will get a roadmap to your first bug.
Information and registration: https://www.securityweek.com/kaspersky-and-securityweek-present-sashome-virtual-event-security-analyst-summit