During the previous post, we discussed the meaning of the different types of attacks, which are extremely complex and involve a large number of targeted actions performed by attackers. In this part, I would like to talk about so-called quantitative research of the attacks used to analyze the maturity level of existing protective technologies and security approaches.
All unusual things have to make one step forward!
In order to describe the method of unknown attacks detection, many authors use the word “abnormality.” An abnormality includes all the attacks and processes within the system that are outside of typical behavior state set (in other words, not typical).
If we define (according to the authors of the article: “Unknown Threat Detection With Honeypot Ensemble Analysis Using Big Data Security Architecture“) the unknown attacks as the set of actions affecting the sensors of the implementer honeypot, we can easily use the obtained information to define the key parameters of the detected attack to find the same parameters in real infrastructure by using probabilistic assessment.
There are special metrics that can be used to describe the model of the unknown attack. Such metrics allow for giving a quantitative evaluation of the unknown attacks within the targeted infrastructure. These metrics are based on the attack graph. In order to understand the way of the calculation of the unknown attack for the given infrastructure, we need to use its simplified network model.
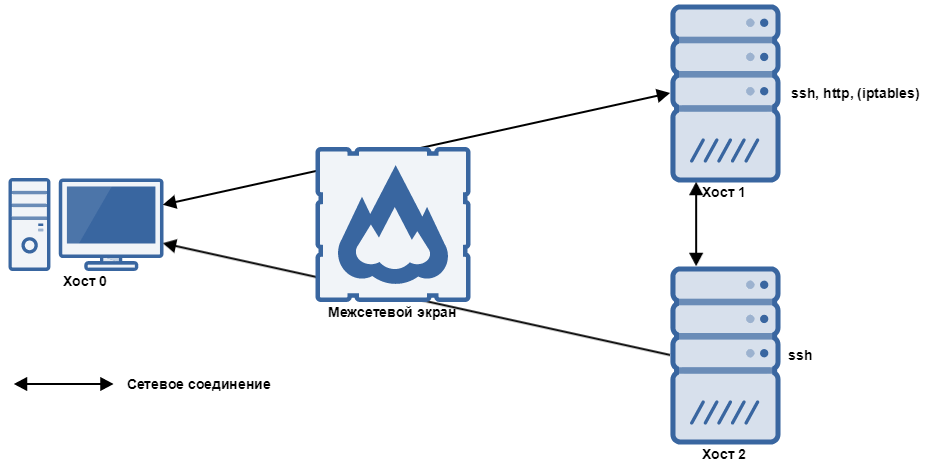
The computer network scheme that we are going to use to give a formal definition of the unknown attack
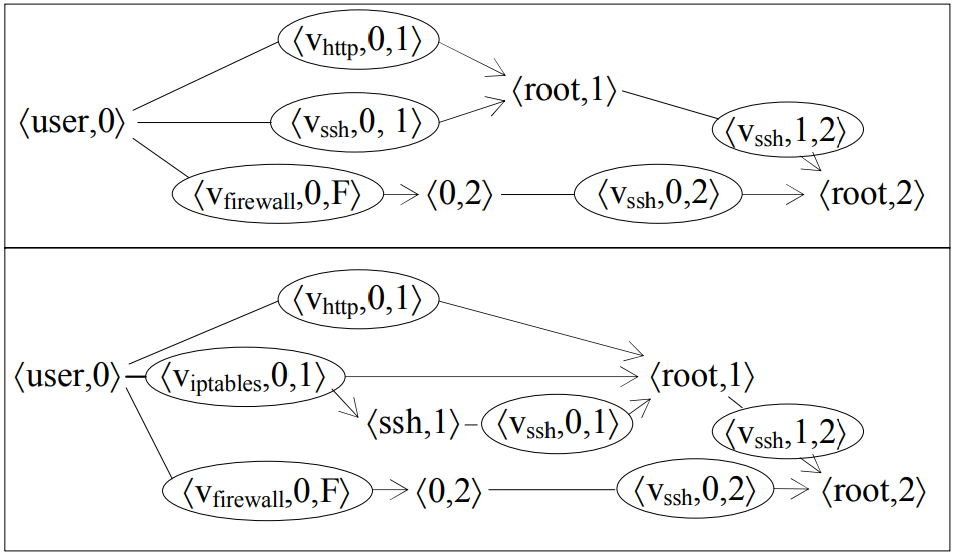
In the simplified model, Host 1 provides SSH remote control service and HTTP-service for data exchange protocol. Host 2 provides only SSH service. Host 0 is the client (user) located behind the firewall relative to the Host 1 and Host 2. The firewall allows inbound connections to Host 1 and outgoing connections from Host 1, as well as all outgoing connections from Host 2. According to the authors of the metrics, the key problem in this network is the ability to gain unauthorized access to Host 2 using the privileges of its root-user. By using this information, we created the attack graph for the given network (the upper part of the image below).
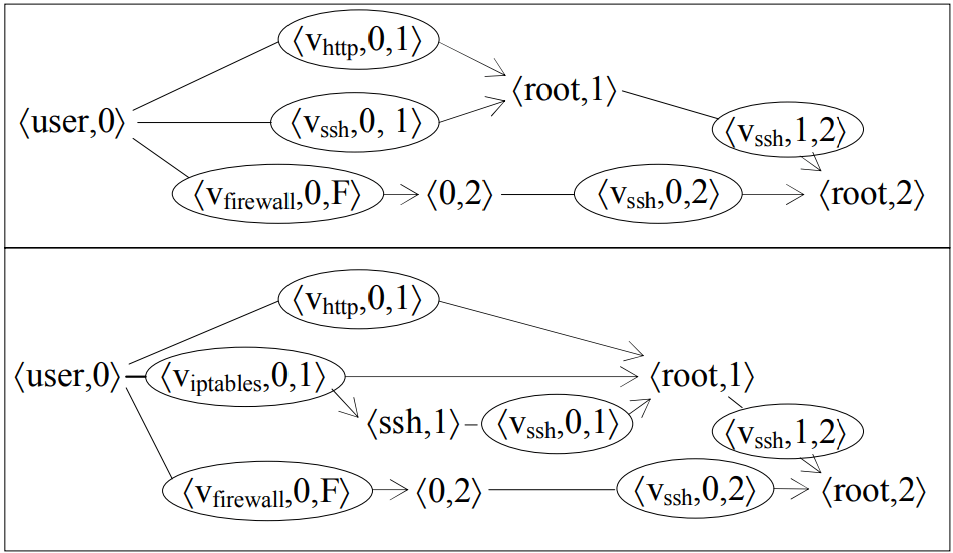
In this image, each <user, 0> pair represents the initial condition, while the <Vssh, 0, 1> element represents the process of unknown (using the term we describe as 0day or unpatched vulnerability) Vssh vulnerability exploitation in SSH service. As a result, this graph clearly shows us that there are three main paths to <root, 2> condition and to gain unauthorized access. At the same time, the attacker will need at least one 0day-vulnerability to create the attack path that includes only Vssh points (keeping in mind that all SSH servers have the same version).
In order to show that the number of unknown attacks depends on the existence of specific systems within the network (including security ones), we can add iptables firewall to the network model, which would allow outbound connections from SSH Host 1 from a strictly defined list of hosts, excluding Host 0. Now take a look at the attack graph for the updated model. It includes two new paths for attacks, which appear as a result of the exploitation of an unknown vulnerability in iptables service.
Based on the definition of the 0day-vulnerability and exploits of each of the services within the given model, the author defines the graph of unknown attacks in the following way: it’s an oriented graph that includes both known and unknown exploits with the points of preconditions connected with post-conditions using the corresponding exploits.
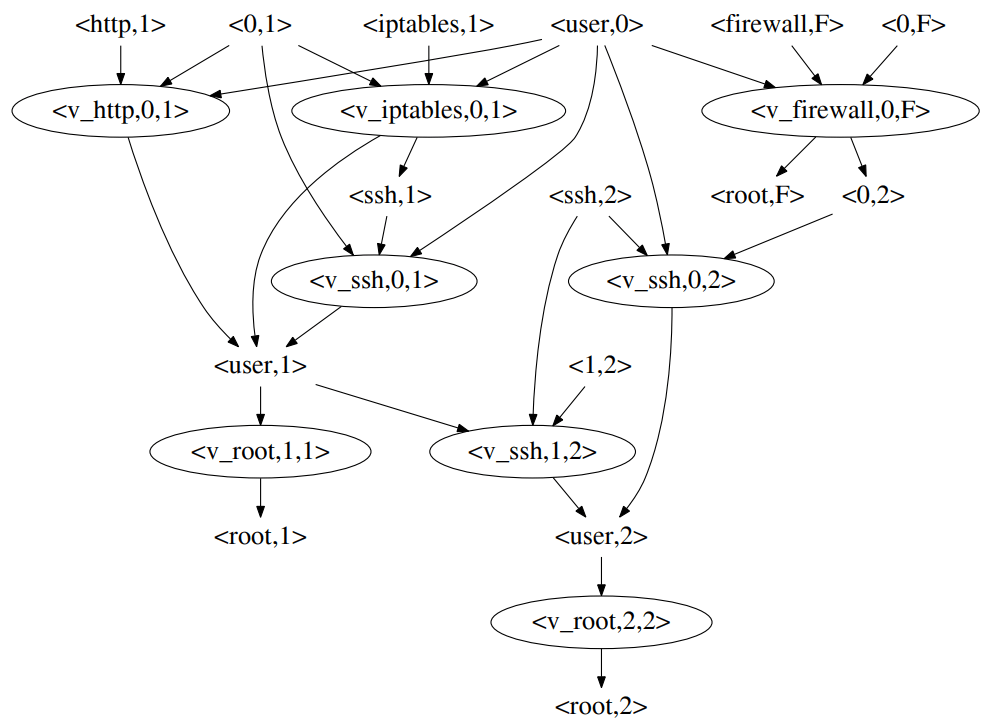
Example of the unknown attack graph
Described models show us the following key requirements for the attack detection system: the number of the attack paths created by the components of the protected network has to be minimum. The protection systems also contain vulnerabilities in their components, which would provide the attacker access to the protected resources, and we need to take this into account. Furthermore, the attack detection system is able to detect them in all stages of the lifecycle, including the last one (e.g., data exfiltration). It may seem like an easy task to detect the attack during all the stages of its implementation; however, in real life conditions, attackers are able to get access to the corporate network, send information to their command centers, and stay within the network for continuous periods of time (in some cases, the attacker may remain undetected for years).
Attack detection methods
Last year, during the Black Hat 2018 conference, keynote speaker Alex Stamos (formerly Facebook CISO) said the following: these days the cybersecurity industry is suffering from the problems of the “puberty period,” and the key issue is the “negativism” of the experts in the industry. By focusing on complex and comprehensive hacking techniques and exotic scientific works, they simply ignore classic and still relevant attack scenarios, which cause serious financial harm and damage to companies all around the world. The attackers are able to reach their goals using the simplest and the most affordable ways. According to Stamos: “It’s time to grow up.” In other words, we need not only analyze the behavior of the attackers but develop new threat detection technologies.
Attack detection methods are divided into two large classes (the classification is according to decision-making approaches): misuse detection and anomaly detection. The first class of methods uses all types of patterns (signatures, policies, indicators of compromise, etc.) to detect malicious activity. For example, the well-known “old school” network IDS/IPS Snort or “brisk” Suricata are based on a huge database of signatures.
One can argue for a long time about the advantages of methods belonging to a particular class, but it’s important to understand that these classes are complementary. Detection of malicious activity in the set of anomalies will allow you to create its signature for rapid detection of this threat in the future.
Anomaly detection methods are interesting for us since they cover all the sets of permissible effects on the protected system, which allows us to identify previously unknown attacks. For algorithms of the methods, there is a noticeable problem: false positives and false negatives (skipping of incidents). Both implementations in the “learning with the teacher” mode and in the self-learning mode (adaptive mode) are possible for all correlation methods.
Where is an anomaly, Bro?
In order to get familiar with the tools for anomaly detection, I recommend the Bro network framework (currently Zeek). It’s a basis for tons of commercial IDSs.
To install Bro on the latest version of Ubuntu, just follow these steps (privileged user is required):
apt-get update && apt-get upgrade
apt-get install cmake make gcc g++ flex bison libpcap-dev libgeoip-dev libssl-dev python-dev zlib1g-dev libmagic-dev swig2.0
wget https://www.bro.org/downloads/bro-2.5.1.tar.gz
cd bro-2.5.1
./configure --prefix=/bro
make
make install
export PATH=/bro/bin:$PATHBefore using Bro, you have to configure it:
- for standalone configuration, it’s enough to specify the interface that will be listened by Zeek (for example, eth0) in the /bro/etc/node.cfg file:
[bro] type=standalone host=localhost interface=eth0 - describe the networks that need to be protected (in /bro/etc/networks.cfg):
192.168.13.0/24 Private IP space - configure the parameters of log processing in /bro/etc/broctl.cfg
Start the IDS:
sudo /bro/bin/broctl[BroControl] > install[BroControl] > start- To stop the IDS:
broctl stop - To restart (after you edit a script):
[BroControl] > stop && check && <point 2> && <pont 3>. - Or:
[BroControl] > deploy.
In fact, the majority of threat detection tools are based on a set of specific templates in order to detect malicious activity. They can be based on detailed signatures and keep specific features of the given malicious software in the traffic. For example, after the fast expansion of WannaCry, experts started updating their IDS/IPS systems with signatures that would detect specific flags within the traffic, which would appear during the process of successful exploitation of SMB protocol. Here’s an example of such a signature:
alert smb $HOME_NET any → any any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response"; flow:from_server,established; content:"|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|"; depth:16; fast_pattern; content:"|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|"; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; metadata: former_category EXPLOIT; classtype:trojan-activity; sid:2024218; rev:1; metadata:attack_target SMB_Server, deployment Internal, signature_severity Critical, created_at 2017_04_17, updated_at 2017_04_17;)No doubt, this type of traffic feature corresponds with a specific exploit. It’s quite difficult to create them before the first attack, thus this solution cannot be used to prevent unknown attacks on the initial level of traffic detailed elaboration. We need new templates, which would be capable of detecting entire classes of attacks or even entire TTPs.
As was mentioned above, we are able to fight with the attack during any stage of its implementation. The latter is the stage when the attack is detected (e.g., the process of bot communication with the C2), the higher is the risk of valuable information loss. Nevertheless, such abnormality templates can be used to detect unusual behavioral scenarios within the network. For example, the increase of the DNS traffic can be the sign of a DNS tunnel creation. However, it can also be a false positive. And the process of false positive mitigation is a totally different story.