As numerous studies have shown, smart houses, smart cars, and smart cities are undeniably beneficial to people in everyday life, but quite often can become a threat to their safety. It is not only a matter of personal data leakage. Just imagine that, for example, a smart refrigerator, affected by a third party at one point or another, would begin identifying expired products as fresh. There is yet another more dismal scenario: the system of a smart car turns the vehicle to the right at high speed, catching the driver unaware…
However, both existing and predictable threats that emerge from home IoT devices are only part of the problem related to the infrastructure around us becoming “smarter”. A technological boom in medicine both encouraged medical institutions to use exclusively information systems in processing data and led to the emergence of new types of technological equipment and personal devices that can be used to interact with traditional systems and networks. This means that the threats that are relevant for them can also be relevant for medical systems.
The article is prepared especially for Securelist.com
Entry Points for Accessing Valuable Data
For the medical industry, the main attack vector is related to personal data and information on the health condition of patients. The first step in evaluating the security level for data is identifying entry points within the infrastructure of medical institutions where healthcare data can be collected, stored, and/or taken advantage of by an evildoer.
Possible entry points can be classified as follows:
- information systems on the computer network of a medical institution (servers, workstations, admin panels for medical equipment, etc.) that access the Internet;
- medical equipment that is connected to an enterprise network;
- medical equipment that is not a network node but connects to a workstation (for example, via USB);
- portable devices of patients (advanced fitness trackers, pacemakers and cardiac monitors, insulin pumps, etc.) and mobile devices that can track health indicators (mobile smartphones and smart watches);
- other wireless information systems (Wi-Fi, Bluetooth, or RF), which can be mobile ECG devices, pulse oximeters, event monitors for tracking the medical condition of high-risk patients, and so on.
For the last three classes mentioned above, a detailed first-hand analysis of specific models related to these classes is required. It is for exactly this reason that those devices deserve an article of their own. For now, we will focus on devices and their components that do not require physical access and are frequently accessible from the Internet.
Portable Devices May Port Medical Histories
We’ve already written the following about the security of portable devices in March of 2015: “Just imagine, if a fitness tracker with a heart-rate monitor is hacked, then any shop owner will be able to track the heart rate of buyers as they look at discounts in the shop. The influence of advertisements on people can be learned in the same manner. Moreover, a hacked fitness tracker with a heart-rate monitor can be used as a lie detector.”
Owing to the increasing accuracy of sensors, gadgets that collect data on the health condition of their owners can potentially be used in serious ambulatory care to assess a patient’s health. However, the level of security for these gadgets has not been developing as fast as their capabilities.
Information that is collected by tracking vital signs can be used by both the owner of the device and the vendor of the infrastructure that the tracking app operates on. For users, the heart-rate parameter can signify that a certain activity should be decreased, specific medicines should be taken, etc., while vendors can send collected data to medical companies that can use it to assess the overall health of the client.
Thus, the main advantage of data collected by a gadget is not the depth of its analysis (any medical examination will yield more accurate results than readings from a fitness tracker) but the ability to evaluate changes in a patient’s health condition dynamically. Scenarios for using the information are limited by the imagination and enterprise of the owner, as well as by laws related to personal data.
If we look at the same piece of information from the perspective of a cybercriminal, then an owner of such a device will have not the most favorable outlook — analysis of certain parameters (for example, heart rate, sleep quality, or average ADL score) allows a criminal to gain an overview of a victim’s health. Any additional information may be provided by a gadget that is connected to the mobile device and is capable, for instance, of measuring the blood pressure or blood sugar levels of its user. After making conclusions about the ailments of a victim, an evildoer can provoke their aggravation.
Attacks to obtain health data can be divided into three basic types: those that violate data privacy, those that compromise data integrity, and those that attack data availability. Main vectors can be defined for each of those.
Types of attack that violate the privacy of medical data:
- man-in-the-middle attacks on a sensor channel between the sensor and the service that stores the sensor’s data;
- unauthorized access to local and remote data storage.
Types of attacks on data integrity:
- unauthorized access to data storage with possible data substitution;
- man-in-the-middle spoofing attacks on channels in order to substitute transmitted data;
- modification (substitution) of data (spoofing attacks) and their transmission to consumers (as a service that stores data or an app).
Attacks on availability:
- ransomware attacks (encryption/deletion of user data).
Entry points for malicious code that commits theft or substitutes data on a mobile device depend on a specific combination of device and software.
Online Medical Data
Yet, I would like to review another entry point in detail — information systems on a medical institution’s network that are accessible from the Internet.
Medical institutions utilize automated healthcare data storage solutions, which store miscellaneous information about patients (diagnosis results, information about prescribed drugs, medical histories, etc.). The infrastructure of such a system may include various hardware and software components, which can be merged into data storage networks and can be accessible from the Internet in one form or another.
Regarding solutions for storage of healthcare data, several software packages, which can be exploited as entry points into medical infrastructure, can be given as examples.
- Hospital information systems (HISs) are software packages that control medical information coming from various sources, including the systems mentioned below.
- Electronic Health Records (EHR) systems are dedicated software that enable storage of structured patient data and documentation of patient medical history.
- Network-attached storage (NAS) refers to dedicated network storage devices, which can be both specialized devices for storing healthcare data or enterprise devices employed in the medical-institution
- DICOM-complaint (Digital Imaging and Communications in Medicine) devices and PACS (picture archiving and communication system) servers are medical information systems based on the DICOM standard and include the following components:
- a DICOM client, which is a medical device that is capable of transmitting data to a DICOM server;
- a DICOM server, which is a hardware and software package that provides for the receipt and storage of data from clients (in particular, these devices can be PACS servers);
- a DICOM diagnostic workstation and DICOM printers, both of which are hardware and software packages that are responsible for processing, visualizing, and printing medical images.
A key feature of the above-mentioned systems is a web interface (a web app) that is used to control them over the Internet. A web interface may have vulnerabilities that can be exploited by an evildoer, who can gain access to valuable information and processes. It is worth reviewing these systems in detail and verifying whether they are accessible from the Internet, i.e. if they are a potential entry point for evildoers.
Electronic Health Records (EHR)
In order to evaluate the number of apps that are available from the outside (from the Internet) and can work with EHR, a list of software employed in these tasks should be created and then a dork list should be organized. Dorks are special search-engine queries that are aimed at finding web components of required software among all of the resources indexed by a search engine.
Here is an example of a dork query that uses Google to search for the login form of EHR software components:
intitle:”<vendor_name> Login” & inurl:<vendor name>
It should be noted that some of the resources found in the search results turned out to be traps for evildoers (honeypots). This fact alone indicates that analysts are seeking to track threats related to medical infrastructure. To check if an identified resource is a honeypot, an IP address should be submitted to a special service, HoneyScore, which, by scanning a number of the resource’s attributes (for example, the hosting provider), reaches a verdict on whether or not the resource is a honeypot. Nevertheless, a significant part of the discovered resources is represented by actual systems.

Each of the discovered web resources is a potential entry point that can be exploited by an evildoer to access the infrastructure. For example, many discovered systems lack protection against an exhaustive password search, which means that a criminal can use brute-force attacks. Then, by using a hacked account, the evildoer can gain privileged access to the system through the interface or find or exploit online vulnerabilities in order to access the system in the future.
Hospital Information Systems (HISs)
A “hospital information system” is quite a vast notion that includes a set of methods and technologies for processing medical information. In our case, we are interested only in the HIS components that have a web interface for controlling and visualizing medical information.
Let’s consider the software of OpenEMR as an example. This software is used in medical institutions as a medical-data management solution, and it is certified by the Office of the National Coordinator for Health Information Technology (ONC). Some of its components are written in the PHP programming language, which means that a potential entry point for an evildoer can be a web server that maintains these OpenEMR components.
The next Google dork query returned 106 search results that meet the following criterion:
inurl:”/interface/login/login_frame.php” intitle:”Login” intext:”Username:”
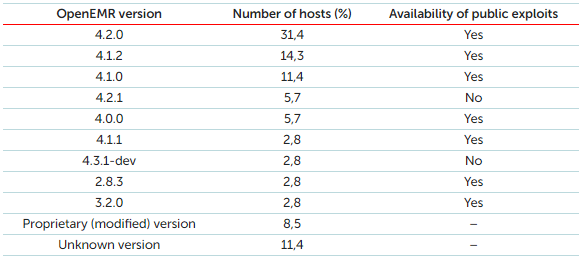
After a quick analysis of the search results, it became obvious that components of the majority of the discovered OpenEMR systems have vulnerabilities, including some critical ones. This means that these vulnerabilities open up the OpenEMR database to being compromised. This comes with the fact that exploits for the discovered vulnerabilities are publicly available.

For example, analyzing different software versions revealed that information had been published on the vulnerabilities for the vast majority of software installed on the hosts.
Network Attached Storage (NAS)
There are at least two types of NAS servers that have been used by medical institutions: dedicated “medical” NAS servers and common ones. While the former have strict security requirements for the data stored on them (for example, compliance with the Health Insurance Portability and Accountability Act), the security of the latter rests on the conscience of their developers and the medical institutions that use this type of NAS in their infrastructure. As a result, non-medical NAS may be left working without any updates for years and thus gather a great number of known vulnerabilities.
A list of dorks should be created to select NAS devices located in medical institutions out of all of the other devices indexed by search engines.
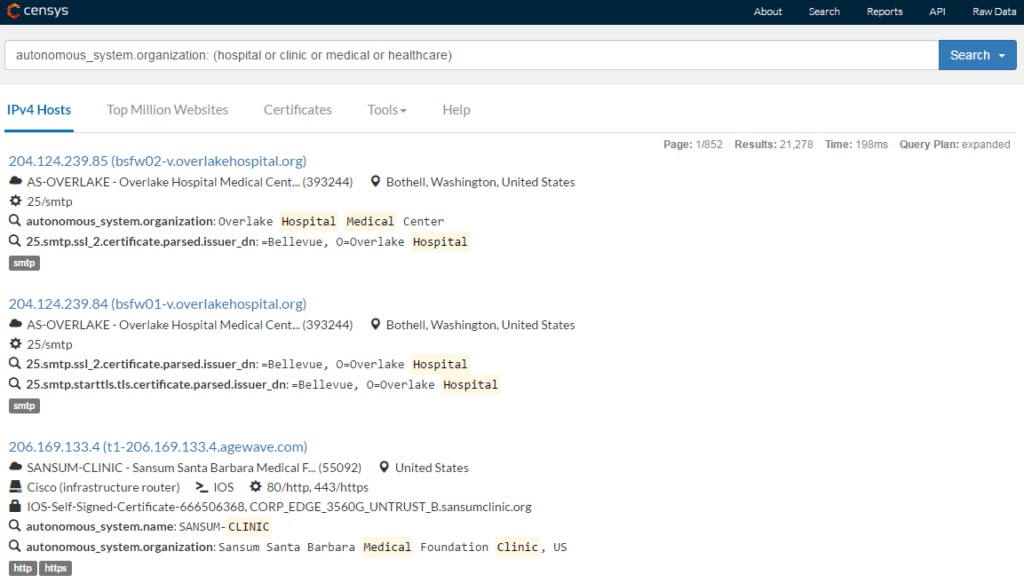
The next query is for the Censys search engine, which specializes in indexing devices with IP addresses and finds all of the devices (workstations, servers, routers, NAS servers, etc.) that belong to companies whose names contain words that directly or indirectly define these companies as medical institutions (“healthcare”, “clinic”, “hospital”, and “medical”):
autonomous_system.organization: (hospital or clinic or medical or healthcare)
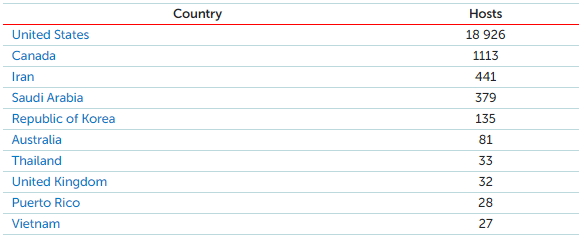
The Censys report, which is shown below, lists the top 10 countries where these hosts are located.
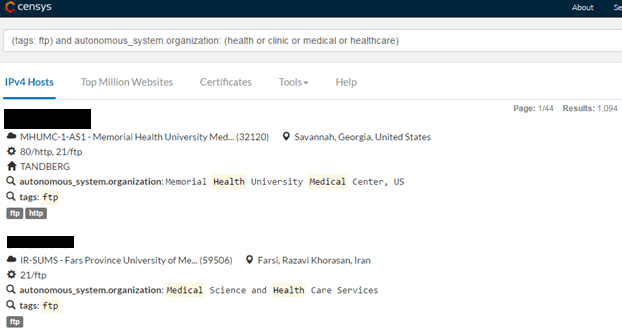
Afterward, only those hosts that are FTP servers can be taken out from the search results that contain the hosts. In order to do this, the query in the search engine should be more specific and, for example, only the hosts that contain an open FTP port and whose banners contain the “FTP” line should be searched for (this is the information that a server sends to a client during attempts to connect to its port):
(tags: ftp) and autonomous_system.organization: (health or clinic or medical or healthcare)
The search results displayed 1,094 hosts with operational FTP servers, which presumably belong to medical institutions.
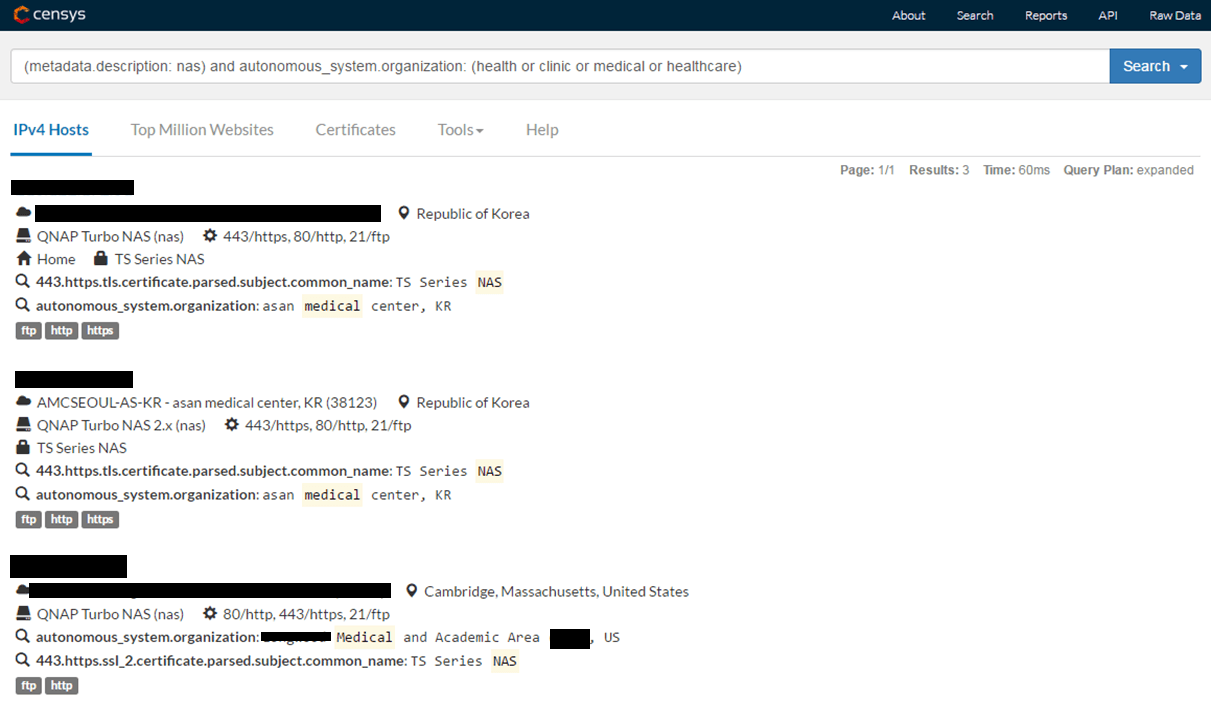
Additionally, a list of vendor-specific NAS devices can be obtained from the narrowed-down search results. For this, the typical characteristics of a device must be known. These may be included in responses from services that are active on the device (for example, an FTP-server response to a connection attempt may contain the name of the device and its firmware version). The next query allows for selection of only those hosts that contain the “NAS” line in their banner (generally, several QNAP Systems models have this property) from all found hosts:
(metadata.description: nas) and autonomous_system.organization: (health or clinic or medical or healthcare)
A ProFTPd web-server release that has vulnerabilities was installed on each of the found NAS. For this release, there is also publicly available and easily accessible information about its exploits.

PACS Servers and DICOM Devices
The most common type of devices that utilize the DICOM format are PACS servers that print patient images that have been received from other DICOM devices.
It is possible to enter the following primitive query in the Shodan search engine to start searching for DICOM devices:
DICOM port:104
Accordingly, the search results will display hosts (mostly workstations and servers) that are used in medical institutions for storing and processing patient DICOM images.
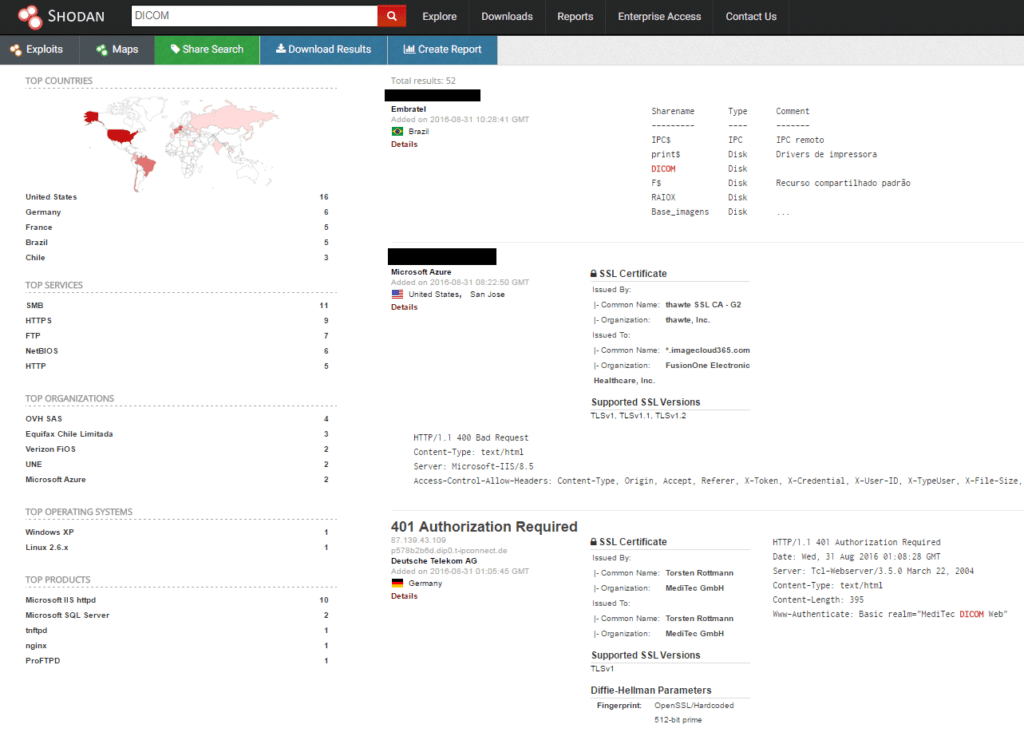
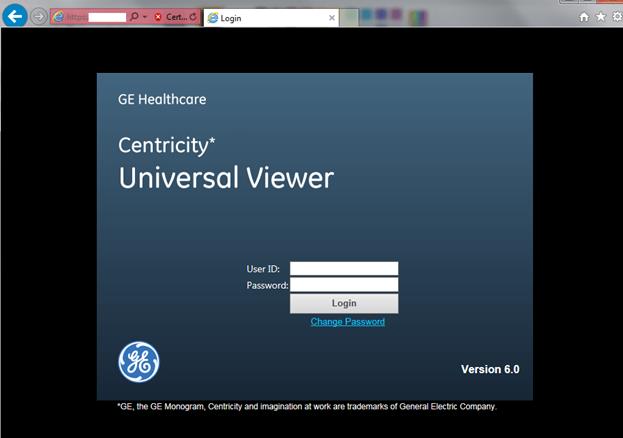
Also, it might be worth searching for diagnostic DICOM workstations, which are dedicated PACS systems used for processing, diagnosing, and visualizing data. As an example, the following query for the Censys search engine can be used:
pacs and autonomous_system.organization: (hospital or clinic or medical or healthcare)
Analysis of the search results may reveal dedicated software for a diagnostic workstation.
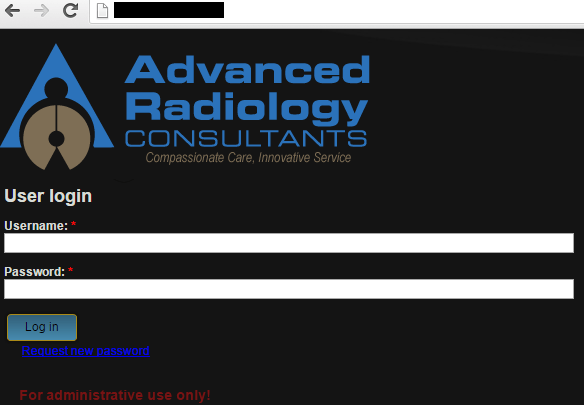
Aside from that, there are also admin panels used to access DICOM servers in the search results.

Non-medical Systems with “Pathologies”
The systems described above handle valuable medical data. Therefore, security requirements for those systems must be high. However, let’s not forget that besides potential entry points, there are dozens of other points an evildoer can use that are not directly related to medical systems but are located in the infrastructure along with valuable data.
Here are several examples of non-medical systems that can be used as a potential entry point into a computer network with the goal of subsequently moving on to resources where medical information is stored:
- any servers (web servers, FTP servers, e-mail servers, etc.) that are connected to the network of an institution and are accessible from the Internet;
- a medical institution’s public Wi-Fi hotspots;
- office printers;
- video surveillance systems;
- SCADA controllers;
- automated systems for controlling mechanical and electrical components of a building (building management systems, BMS).
Each of the mentioned systems may have a vulnerability that can be taken advantage of by an evildoer in order to gain access to medical infrastructure.
For example, the popularity of the Heartbleed vulnerability can be evaluated. This requires entering the following query into the Censys search engine:
autonomous_system.organization: (hospital or clinic or medical or healthcare) and 443.https.heartbleed.heartbleed_vulnerable: 1
The search engine showed 66 hosts that met the criteria and were potentially vulnerable to Heartbleed. Additionally, this was after the existence of the vulnerability, and its dangers had been given wide coverage by the mass media. Generally speaking, when referring to Heartbleed, it should be noted that the problem is global in nature. According to a report by the founder of Shodan, approximately 200,000 websites still remain vulnerable.
Stay Healthy
In order keep evildoers from stealing medical data from institutions, we, along with taking essential security measurestypical for enterprise infrastructure, recommend doing the following:
- exclude from external access all of the information systems that process medical data or any other patient-related data;
- all of the medical equipment that connects to a workstation (or is a network node) should be isolated in a dedicated segment, while the operational parameters of the equipment can be modified by using the workstation (or remotely);
- any online information systems should be isolated in a “demilitarized” zone or completely excluded from an enterprise network;
- continuously monitor medical-system software for updates and update software regularly;
- change default passwords that are set up for the login forms of medical systems and delete unwanted accounts from the database (for example, test accounts);
- create strong passwords for all accounts.