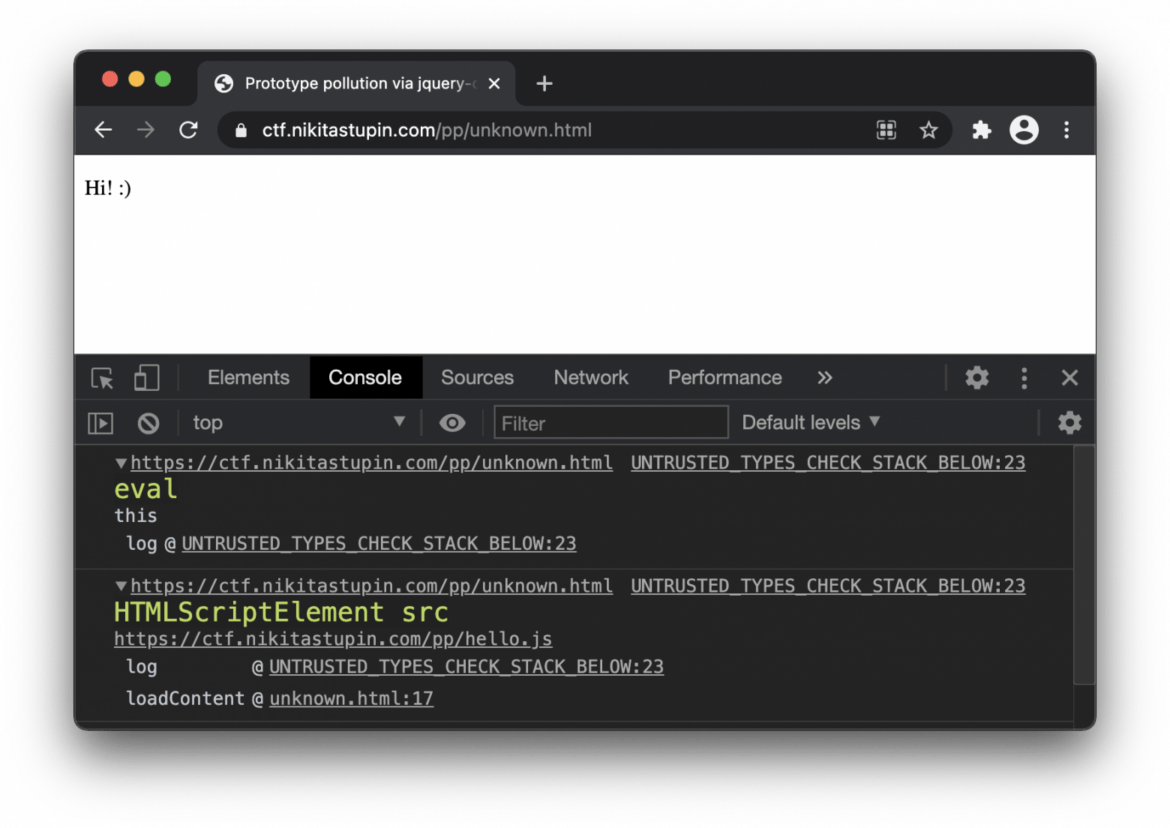
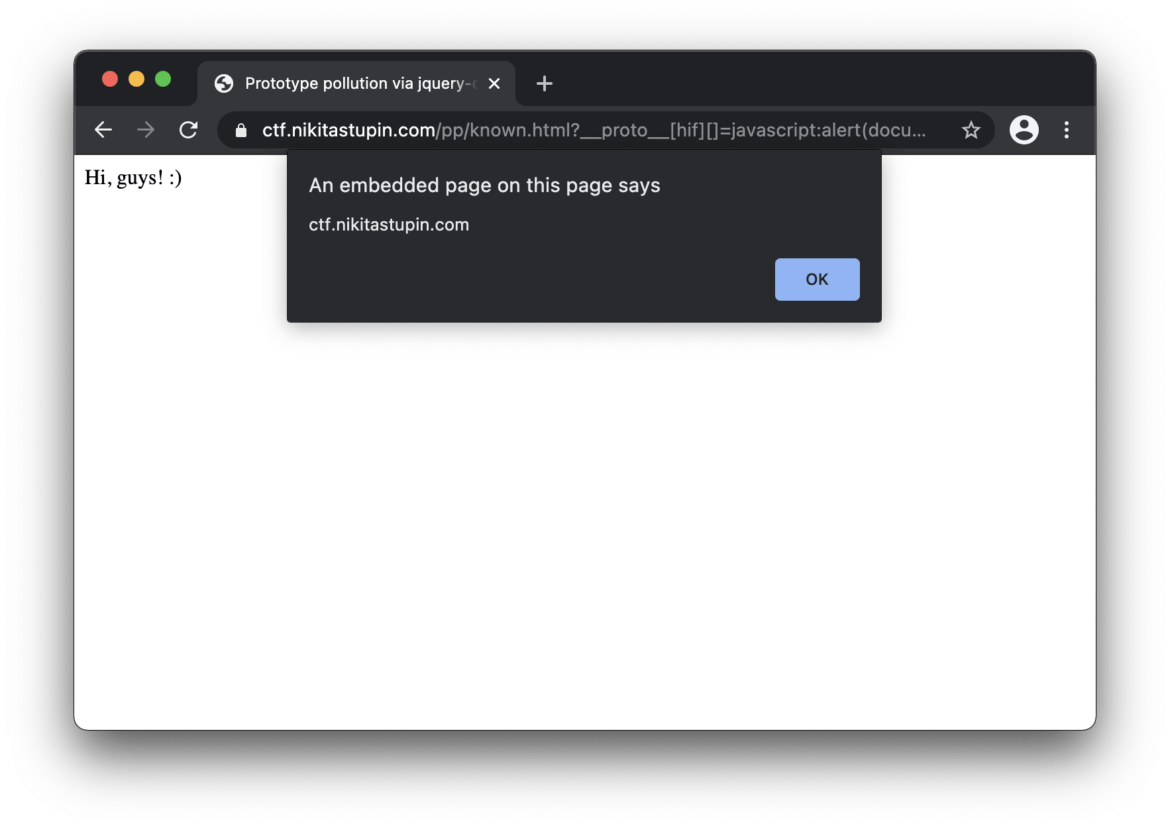
Finally, the English version of “JavaScript prototype pollution: practice of finding and exploitation” article is prepared. Using the techniques Nikita Stupin discovered CVE-2020–28460 in multi-ini parser and a vulnerability in the merge-deep package. With the first one, everything went smoothly, but with the second one, a funny situation came out: after sending the report, the maintainer did not get in touch for a long time, and as a result, GitHub Security Lab found the same vulnerability, managed to reach the maintainer earlier and registered it (GHSL-2020–160). All details related to these vulnerabilities, discovery and exploitation techniques, and recommendations on how to protect your applications are collected in the article.
security research
If you regularly monitor bug bounty reports, you’ve seen “JavaScript prototype pollution” titles. Nikita Stupin decided to dig deeper into the category of vulnerabilities, impacting JavaScript applications, and prepared the practical guide of its discovery and exploitation. Soon we will also prepare an English version of the paper, but currently, you have to manage by yourself to translate it.
Once bug hunting becomes a race of known misconfigurations and CVE detection, automation is required:
- monitor daily #BugBountyTips and CVEs;
- filter results with trendy potential;
- get alerts on time (13:37 UTC +0).
“Bug Hunting Hub” is a Telegram channel with my notes and bot notifications.
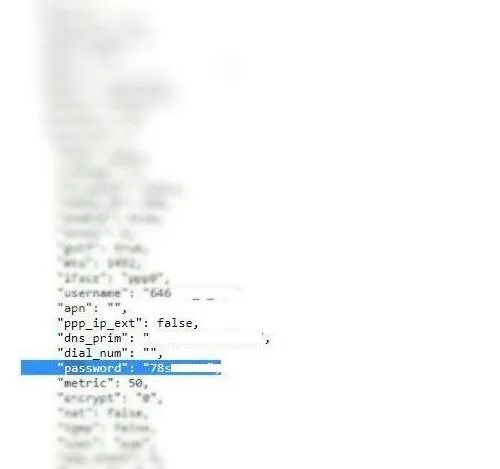
Earlier, I’ve already published information about the critical vulnerabilities and backdoors in D-Link DIR-620 (RevG), that I’ve discovered and submitted to the vendor. The D-Link DIR-620 routers is a model of router, that popular in Russia and CIS countries (most home routers are located behind their ISP’s NAT, which is why these routers don’t appear in the statistics) due to one of the ISPs delivered to its customers (this conclusion is based on the fact that the router is provided as part of the standard customer contract and the hardcoded credentials contain the name of the ISP in the login string).
I’m pleased to join the CFP board of @BSidesCairo 2020. The region of the event is full of rough diamonds in terms of security research. Rise and shine, researcher: https://t.co/jjrRxDEthV pic.twitter.com/5yZAVExPhl
— Denis Makrushin (@difezza) September 20, 2019