Last year we met in Serbia. This time the amazing place can be described in three words: hot, wet, bright.
security architecture
Начало года — это еще и начало сезона подготовки дипломных работ. А это значит, что у меня наступает сезон формулирования тем для студентов факультетов и кафедр информационной безопасности в ведущих вузах. Я собрал свои рекомендации и лайфхаки для подготовки твоего первого ИБ‑исследования.
Service-oriented architecture increases technical abilities of attacker to move laterally and maintain multiple pivot points inside of compromised environment. Microservice-based infrastructure brings more challenges for security architects related to internal event visibility and monitoring.
The research paper published by Alexander Barabanov in “Cybersecurity Issues” provides helpful resources to application and product security architects, software, and operation engineers on existing architecture patterns to implement trustworthy logging and audit process in microservice-based environments. We performed threat modeling for typical architecture pattern of logging system, defined threat mitigation strategy, and, as a result, provided bunch of high-level security requirements for audit logging system.

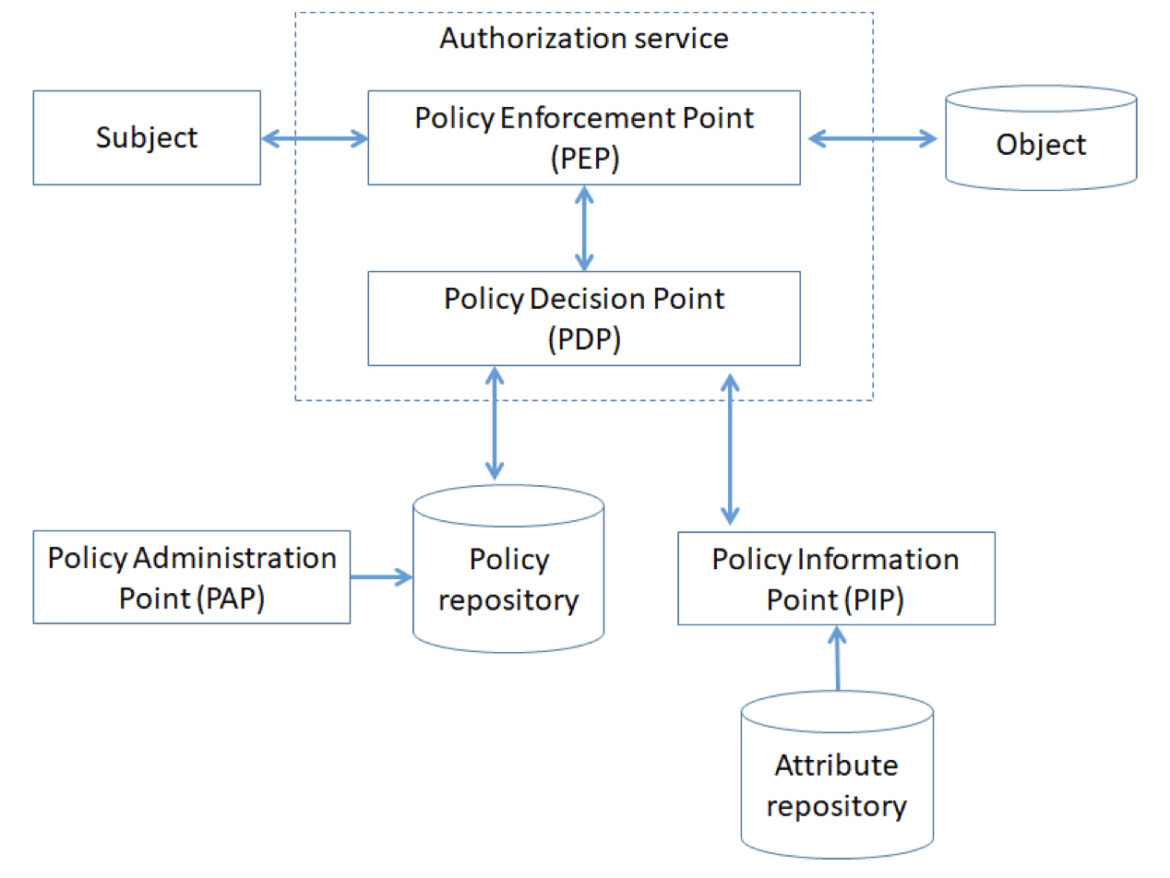
Authentication, Authorization, and Audit (AAA) in microservice-based architecture is a cornerstone for any scale applications. Multiple “best practices” by technology leaders, multiple recommendations by industry influencers. What is relevant to your product design and should be implemented?
We published the survey deliver the AAAnswers with the criteria for choosing the right one for your application security architecture: “Authentication and authorization in microservice-based systems: survey of architecture patterns.”
Objective: the aim of this study is to provide a helpful resource to application security architect and developers on existing architecture patterns to implement authentication and authorization in microservices-based systems.