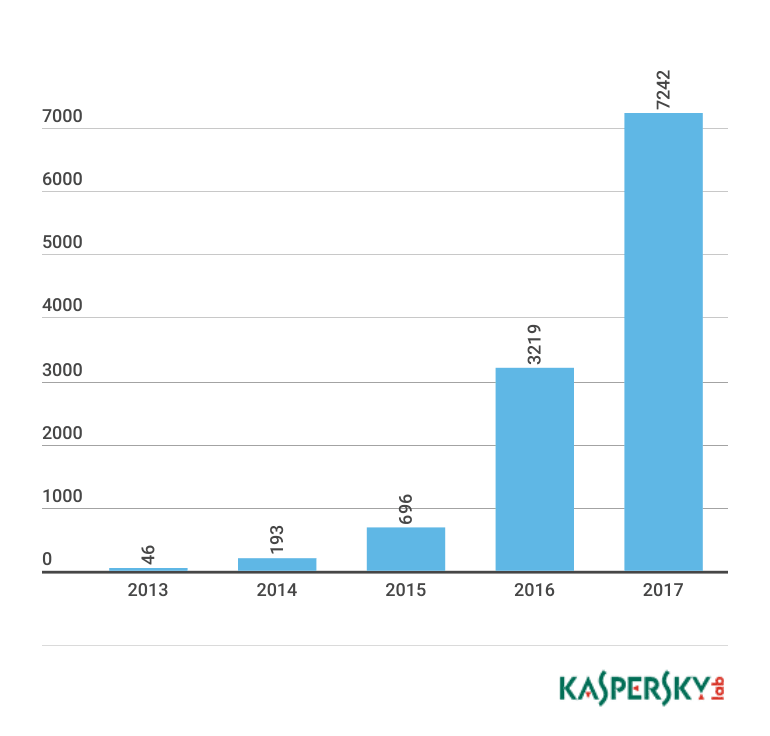
According to Gartner, there are currently over 6 billion IoT devices on the planet. Such a huge number of potentially vulnerable gadgets could not possibly go unnoticed by cybercriminals. As of May 2017, Kaspersky Lab’s collections included several thousand different malware samples for IoT devices, about half of which were detected in 2017.
The article is prepared jointly Vladimir Kuskov, Mikhail Kuzin, Yaroslav Shmelev, Igor Grachev especially for Securelist.com
Statistics
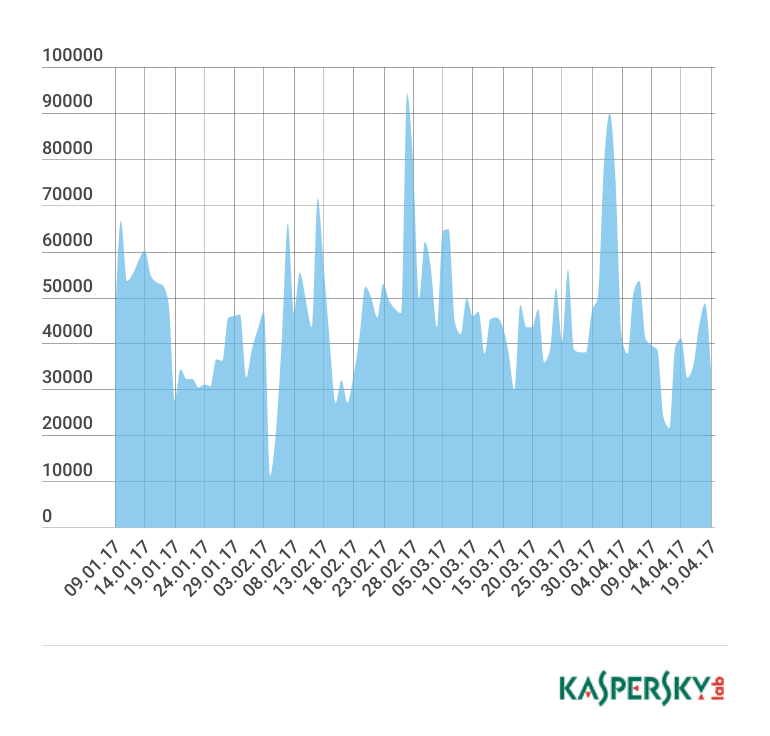
We set up several honeypots (traps) that imitated various devices running Linux, and left them connected to the Internet to see what happened to them ‘in the wild’. The result was not long in coming: after just a few seconds we saw the first attempted connections to the open telnet port. Over a 24-hour period there were tens of thousands of attempted connections from unique IP addresses.
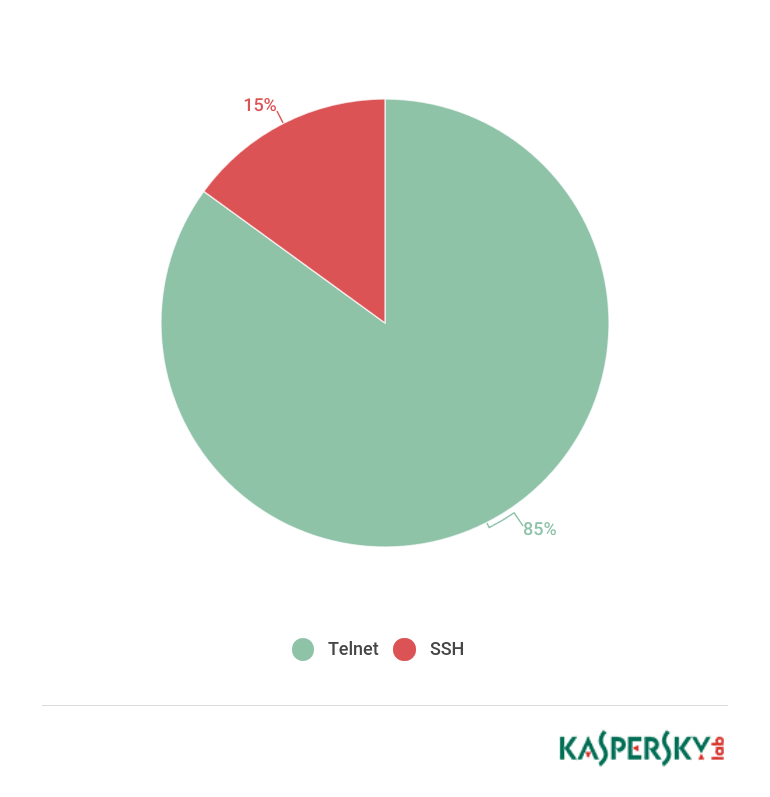
In most cases, the attempted connections used the telnet protocol; the rest used SSH.
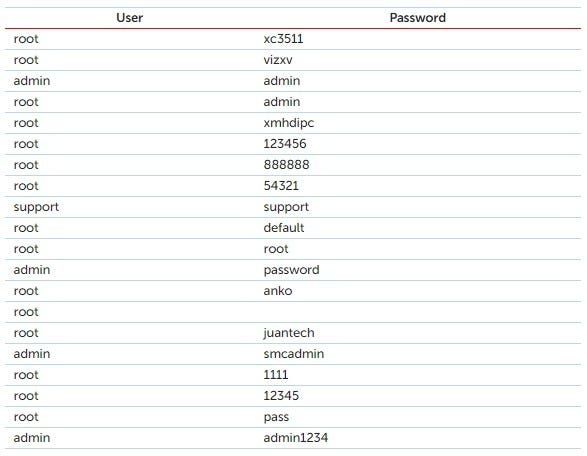
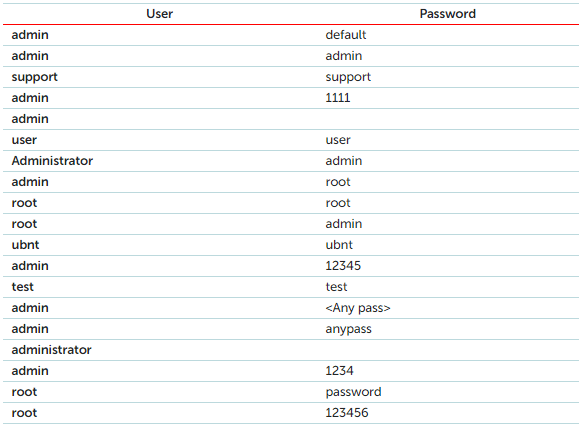
Below is a list of the most popular login/password combinations that malware programs use when attempting to connect to a telnet port:
Here is the list used for SSH attacks. As we can see, it is slightly different.
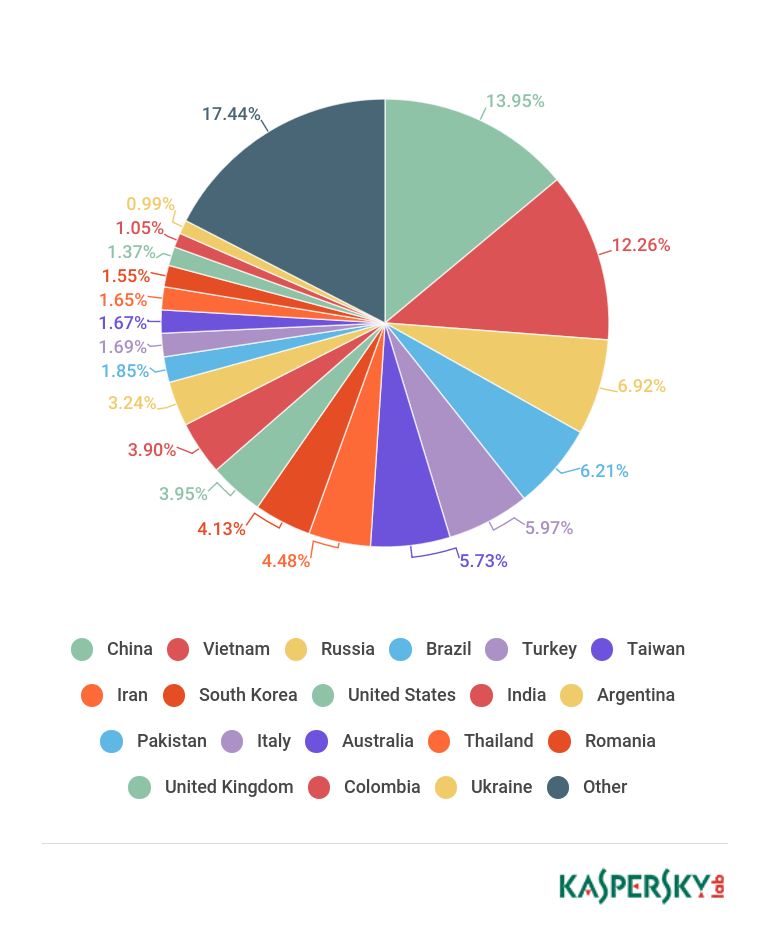
Now, let’s look at the types of devices from which the attacks originated. Over 63% of them could be identified as DVR services or IP cameras, while about 16% were different types of network devices and routers from all the major manufacturers. 1% were Wi-Fi repeaters and other network hardware, TV tuners, Voice over IP devices, Tor exit nodes, printers and ‘smart-home’ devices. About 20% of devices could not be identified unequivocally.
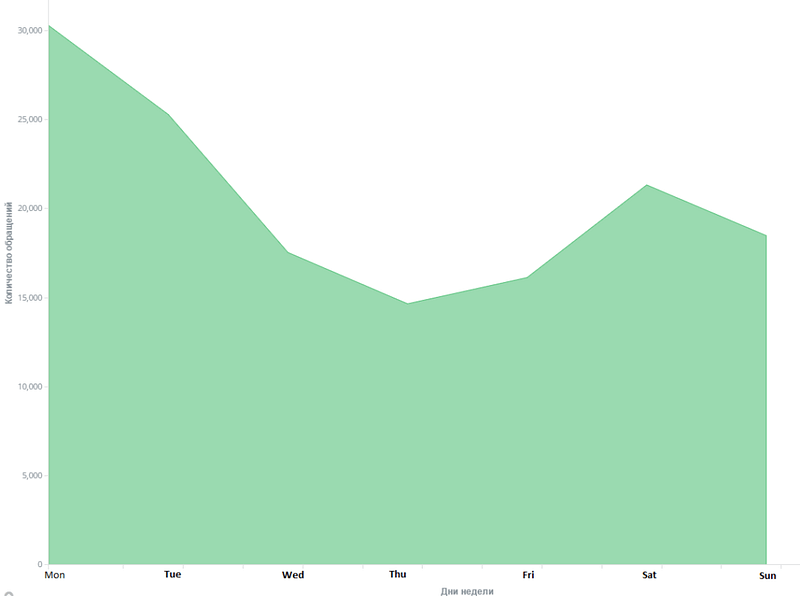
Distribution of attack activity by days of the week
When analyzing the activities of IoT botnets, we looked at certain parameters of their operations. We found that there are certain days of the week when there are surges in malicious activity (such as scanning, password attacks, and attempted connections).
It appears Monday is a difficult day for cybercriminals too. We couldn’t find any other explanation for this peculiar behavior.
Conclusion
The growing number of malware programs targeting IoT devices and related security incidents demonstrates how serious the problem of smart device security is. 2016 has shown that these threats are not just conceptual but are in fact very real. The existing competition in the DDoS market drives cybercriminals to look for new resources to launch increasingly powerful attacks. The Mirai botnet has shown that smart devices can be harnessed for this purpose — already today, there are billions of these devices globally, and by 2020 their number will grow to 20–50 billion devices, according to predictions by analysts at different companies.
In conclusion, we offer some recommendations that may help safeguard your devices from infection:
- Do not allow access to your device from outside of your local network, unless you specifically need it to use your device;
- Disable all network services that you don’t need to use your device;
- If the device has a preconfigured or default password and you cannot change it, or a preconfigured account that you cannot deactivate, then disable the network services where they are used, or disable access to them from outside the local network.
- Before you start using your device, change the default password and set a new strong password;
- Regularly update your device’s firmware to the latest version (when such updates are available).
If you follow these simple recommendations, you’ll protect yourself from a large portion of existing IoT malware.