A live story told by a virus analyst about research on RCS and Finspy


Denis Makrushin: Information security industry has well demonstrated how versatile it is over the past few years. While just about 5 years ago the business in this area relied solely on protection against cybercriminals and their “metabolic byproducts”, now highly controversial players are entering the stage. Thus, for example, the sale of “weapons”, namely exploits, has became widespread. Now anyone (well, almost anyone, as the price of such weapons may be a six-digit figure or even higher) can acquire the means of vulnerability exploitation and use it at their discretion. This can be compared to sales of live ammunition.
However, the market has gone even further, and now some businessmen offer a full Trojan for sale, chock full of antidebugging features and with a functionality that will hold its own against the most technologically advanced members of the cybercrime black market. This is comparable with the sale of a complete well-equipped fighter plane. So it is a few of such “fighters” that I am going to talk about..
Business-to-government: RCS
 Sergey Golovanov: Back in mid-2012 we (the virus laboratory – Editor) received a message that contained the file adobeupdate.jar. It was a sample for MacOS platform. Our virus analysts immediately sent it to me for a detailed analysis.
Sergey Golovanov: Back in mid-2012 we (the virus laboratory – Editor) received a message that contained the file adobeupdate.jar. It was a sample for MacOS platform. Our virus analysts immediately sent it to me for a detailed analysis.
Inside this instance of malware nothing was encrypted – all read like an open book, and as a consequence, the next day other antivirus companies began publishing information on a new attack which they codenamed Crisis. The fact is that Crisis was the name of one of the modules (here we must thank the Objective C programming language for naked code). RCS files for Windows are written in C++. To help the program avoid the searchlight of anti-virus, its creators have not provided any methods to protect it from the analysis, which is typical for software used for targeted attacks.
The jar file also contained a sample for Windows platform with the functionality similar to that of the Mac one. It contained a funny line: “elementary!PenguiNs;-)SingingHarekrishna_”. At first I thought it was an Easter egg of some sort, but the low-level analysis conducted by my colleague Nicolas Brulé demonstrated that it was not just developers having fun. The fact is that Skype, a famous IM utility, can connect plugins that allow the user to change his or her voice, use all sorts of custom emoticons, etc. A developer who wants to release such a plugin must get it signed by Microsoft, for which the following is required: indication of the full path to the plugin, calculation of MD5 for all the files of the plugin, and specifying a certain special something. In our case, the certain special something was the string we found, intended to be used as a signature for a plugin whose purpose was to intercept all Skype calls. That was an interesting exclusive feature that we have never encountered before this malware, we have never seen it anywhere else. Usually virus makers hack everything inside Skype, but the idea of installing new plugins on top of Skype had not yet occurred to anyone.
Headers of the e-mail received by the antivirus laboratory
All the strings that the creators did not remove during compilation contained an acronym, “RCS”. RCS, also known since 2011 as a Remote Control System, was designed, according to Wikileaks, by HackingTeam, a company that helps national governments to spy on their citizens.

Occurrences of the RCS acronym in a malicious program for MAC platform

The very mysterious phrase which turned out to be the certain special something
Let’s move on. In the course of the analysis we found an exploit that loaded payload from the following URL: rcs-demo.hakingteam.it. Plus, in the sample for Mac we found paths to compilation files, and they looked something like this: /Users/guido. At the same time we found a LinkedIn account owned by a user named Guido *** who indicated HackingTeam as his place of work.
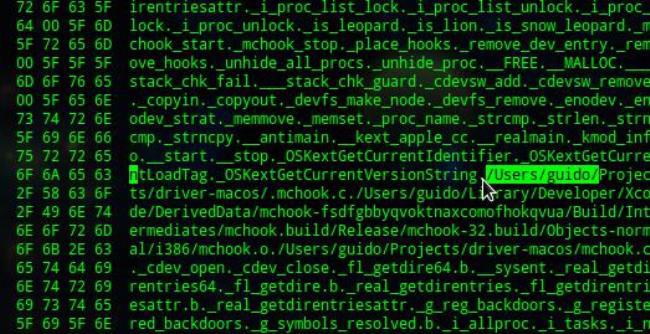
Username guido visible in the malware code
Hunt for exploits that the malware used to spread itself showed that we have caught 0-day in Adobe Flash Player. The developers then assigned it CVE-2010-3333. Then we looked at CVEs of all the exploits that we found in the sample. JAR file is an archive, so you can see the dates when the files have been added. So, the files got into this archive a few months before the discovery of the CVE. It followed that for several years the guys from HackingTeam have owned 0-day (more than one), and therefore, methods for distribution of RCS.
One of the key features of this malware is its self-renewal functionality and the ability to download additional modules. Given the fact that one of the main purposes of RCS is spying on a suspect’s computer, I shudder from the thought that a developer of the malware can upload some interesting and illegal content (e.g. child pornography) to the victim’s computer, and then make the virus remove oneself from the computer. In other words, the object of surveillance can be very easily framed. In this case, no study can detect the fact that there was malware in the system at some moment in the past, because the malware in question, after removing itself, rewrites the space with random data.
After our publications in the media about this malware, the guys from HackingTeam started avoiding our monitoring systems by breaking all RCS modules into separate files. In other words, the system is no longer in one piece.
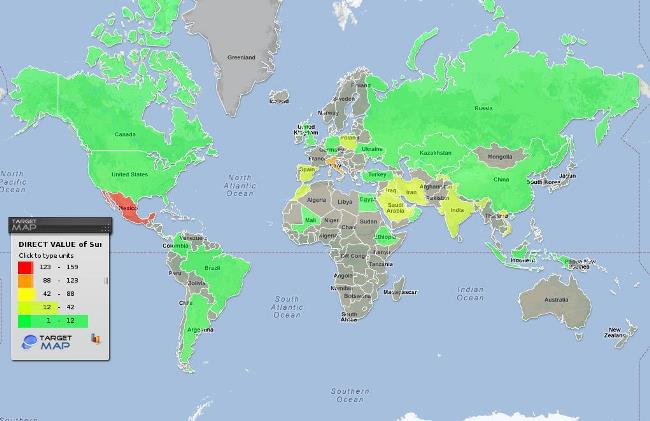
The total number of reported attempts to install RCS on users’ computers worldwide, January 2012 – February 2013
So, RCS has the following features:
- The mechanism of self-propagation via USB:
- Using the standard Autorun.inf mechanism (like most worms detected by KL as Worm.Win32.AutoRun);
- Using a false “Open folder to view files” entry (a popular technique used for self-propagation of worms, in particular the Kido/Confiker worm);
- Using the vulnerability CVE-2010-2568 (Stuxnet used it for self-propagation through LNK files).
- Infecting vmWare virtual machines with copying itself to autostart folder of the virtual disk.
- Infecting BlackBerry and Windows CE mobile devices.
- The mechanism of self-renewal.
- Using AES encryption algorithm to work with files and management servers.
- Installation of drivers.
This invasion: Finspy/Finfisher
Our first meeting with the second brightest representative of government malware also happened in mid-2012, when the first samples of Finfisher and mobile samples of Finspy were discovered. I thought at first that the analysis of malware will go as easy as it happened with HackingTeam’s product. However, Gamma (the vendor that developed Finfisher/Finspy – Editor) presented unexpected surprises.
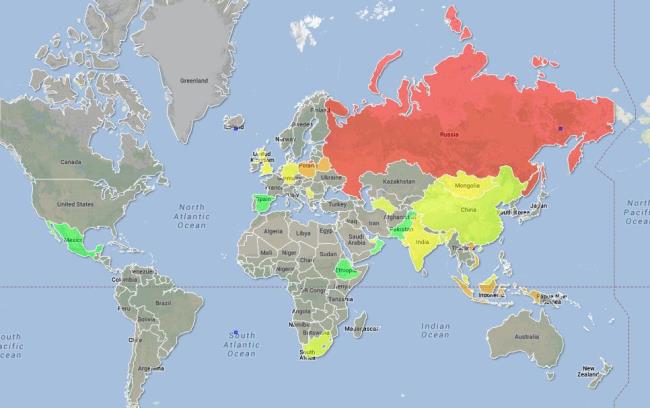
Total number of attempts to install FinSpy recorded for the period of June 2012 – June 2013
We immediately wondered whether Finspy can execute arbitrary code. While finding this out for RCS by disassembling the protocol it uses to communicate with the command center was easy, in the case of Gamma’s product it was much more difficult – the disassemblers went haywire from the abundance of instructions like EB FF (a -1 byte jump which results in re-entering a half of the jump instruction). Repeat after every 10 instructions. If you try to watch the whole thing in the IDA then you need to write a custom script that filters this vile stuff.
Anti-debugging was only the first circle of hell. The next thing I had to deal with was packing, then cryptors, then virtual machines, then cryptors again, and only then I saw the lines of code, which, in turn, have been encrypted in completely different ways. In the end, when we had the infecting code extracted and understood what infiltrates where, we faced a problem again. While trying to intercept the Trojan’s calls to the command center, we realized that the malware has a special cryptor that decrypts and encrypts blocks of code at runtime, on the fly. Therefore, dumping it was practically useless. Finspy also was a bootkit and had methods to counter the kernel level debuggers.
We found a huge buffer where the malware stored commands as opcodes (operation codes – Editor), which hindered reading. Gamma has viruses for many platforms, including mobile platforms. I assumed that the protocol they use to communicate with the command center must be one and the same. Especially as a mobile app is much easier to analyze without various twisted and turned antidebugging mechanism…
Configuration of the Android sample
Unlike RCS that could increase its privileges in the system, Finspy did not have code responsible for escalating privileges. The developers assume alternative ways of spreading malware, e.g., at the level of ISP access (classic MitM, in which malware code is infiltrated into binaries downloaded by a criminal and then everything goes through UAC): simply speaking, it means that when the offender downloads any exe file from the Internet, his provider inserts a Trojan into this file on the fly – Editor).
Nevertheless, the main question remained: whether or not this malware has a feature that allows execution of arbitrary code (for example, download and run a new Trojan with a new functionality – Editor)? The Android sample contained operating codes to execute arbitrary code: download_and_execute, execute_shellcode and the like! So, the answer to the question is as follows: the feature exists, and the malware can potentially execute arbitrary code, but in the samples we found this functionality is missing. We can assume that there is some pro version of the Trojan in which it is implemented.
Instead of conclusion
In recent years, the world has undergone significant changes of which the users have learned not so long ago: the discovery of software used as cyber weapons and as means of cyber-espionage.
Private companies have appeared that, according to information on their official websites, develop and offer software for law enforcement agencies to collect information from users’ computers. Countries that do not have appropriate technical capabilities can buy software with similar functionality from private companies. Despite the fact that most countries have laws prohibiting the creation and distribution of malware, spyware is offered with little or no masking of their functions.
At present, such companies are few, and there is almost no competition in this market, which creates favorable conditions for the emergence of new players and the beginning of the technological race between them. As far as we know, these companies do not hold any responsibility for the further fate of the software they created that can be used for surveillance, international espionage, or the traditional purpose of common cybercriminals, personal gain.
The situation is complicated by the possibility of such programs appearing on the open market, where they can be resold by dummy companies to anyone, anytime. In short, this is only a beginning…
Some more details
About FinSpy and detects in Russia…
Many of you are probably surprised that Russia is painted red on the FinSpy infections map. During our investigation, we had three main theories to explain this:
1. Some organization in Russia has bought and now uses this software.
2. Foreign law enforcement bodies are watching people on the territory of Russia.
3. Someone is using a stolen version of the software.
But the reality was quite different…
Everyone knows that the web has a large number of services that offer checking files for detection by antiviruses. So, all the cases of FinSpy detection in Russia are not live users but robots that use trial versions of Kaspersky Lab’s products on virtual machines. Now the current Russia and FinSpy theory is that someone conducts regular checks on FinSpy detection by antivirus on servers located in the territory of Russia. That’s it folks.
About FinSpy, drug lords, and drones…
To capture Miguel Angel Trevino Morales, the leader of a Mexican criminal organization, the U.S. Navy did not use any drones, which are usually launched on the Mexico border. Instead, intelligence agencies used wiretapping and FinSpy software to find out the drug lord’s location. Read more.