A distributed denial-of-service (DDoS) attack is one of the most popular tools in the cybercriminal arsenal. The motives behind such attacks can vary – from cyber-hooliganism to extortion. There have been cases where criminal groups have threatened their victims with a DDoS attack unless the latter paid 5 bitcoins (more than $5,000). Often, a DDoS attack is used to distract IT staff while another cybercrime such as data theft or malware injection is carried out.
The article is prepared especially for Securelist.com
Almost anyone can fall victim to a DDoS attack. They are relatively cheap and easy to organize, and can be highly effective if reliable protection is not in place. Based on analysis of the data obtained from open sources (for example, offers to organize DDoS attacks on Internet forums or in Tor), we managed to find out the current cost of a DDoS attack on the black market. We also established what exactly the cybercriminals behind DDoS attacks offer their customers.
DDoS as a service
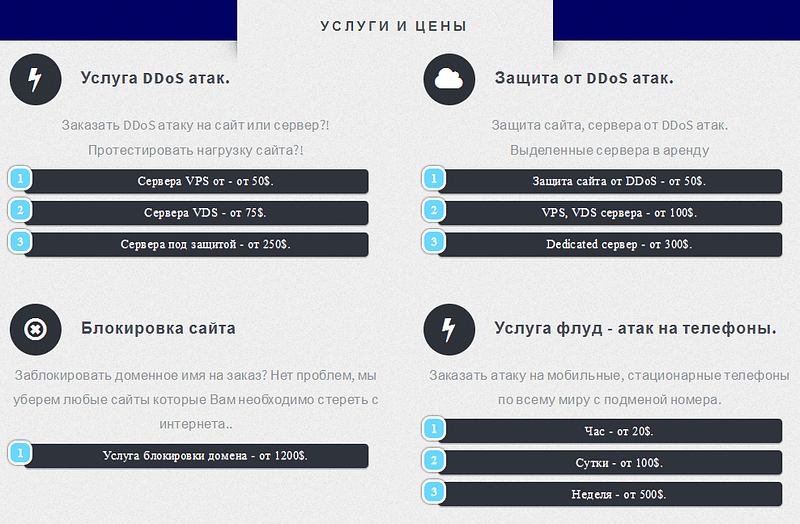
Ordering a DDoS attack is usually done using a full-fledged web service, eliminating the need for direct contact between the organizer and the customer. The majority of offers that we came across left links to these resources rather than contact details. Customers can use them to make payments, get reports on work done or utilize additional services. In fact, the functionality of these web services looks similar to that offered by legal services.
Example of a web service for ordering DDoS attacks that looks more like the web page of an IT startup than a cybercriminal operation
These web services are fully functional web applications that allow registered customers to manage their balance and plan their DDoS attack budget. Some developers even offer bonus points for each attack conducted using their service. In other words, cybercriminals have their own loyalty and customer service programs.
DDoS service advertised on a Russian public forum offering attacks from $50 per day
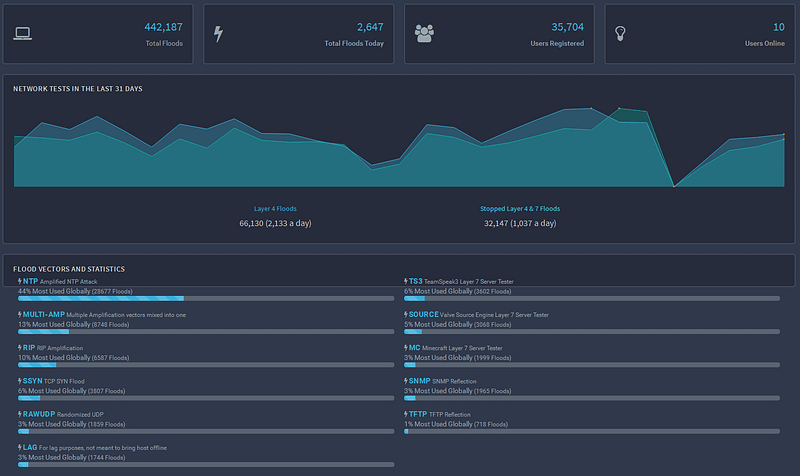
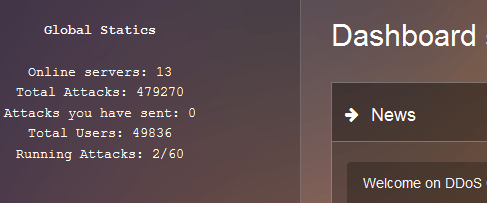
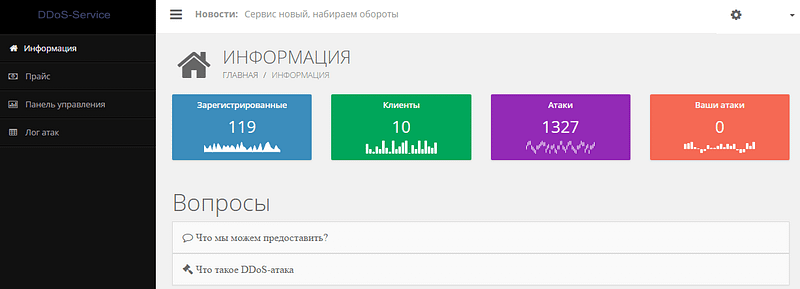
Some of the services we identified contained information on the number of registered users, as well as data on the number of attacks carried out per day. Many of the web services offering DDoS attacks claimed to have tens of thousands of registered accounts. However, these figures may be inflated by the owners of services to make their resources look more popular.
Statistics provided by one service to demonstrate its popularity with DDoS customers (479270 implemented attacks)
Statistics provided by one service to demonstrate the popularity of DDoS attack scenarios
Information about the popularity of a DDoS service
Rates for DDoS
The special features emphasized in the adverts for DDoS services can give a particular service an advantage over its competitors and sway the customer’s choice:
- The target and its characteristics. A cybercriminal that agrees to attack a government resource will attract customers who are interested in this particular service. The attacker can ask for more money for this type of service than they would for an attack on an online store. The cost of the service may also depend on the type of anti-DDoS protection the potential victim has: if the target uses traffic filtering systems to protect its resources, the cybercriminals have to come up with ways of bypassing them to ensure an effective attack, and this also means an increase in the price.
- Attack sources and their characteristics. This factor can determine the price the attackers ask for conducting their attacks. The cheaper it is for a criminal to maintain a botnet (defined, for example, by the average cost of infecting a device and including it in a botnet), the more likely they are to ask for bargain-basement prices for their services. For example, a botnet of 1000 surveillance cameras may be cheaper in terms of organization than a botnet of 100 servers. This is because cameras and other IoT devices are currently less secure – a fact that is often ignored by their owners.
- Attack scenario. Requests for atypical DDoS attacks (for example, the customer may ask the botnet owner to alternate between different methods of DDoS attacks within a short period of time or implement several methods simultaneously) can increase costs.
- The average cost of a DDoS attack as a service in a particular country. Competition can cause cybercriminals to raise or lower the cost of their services. They also try to take into consideration the ability of their audience to pay and devise their pricing policy accordingly (for example, a DDoS attack will cost US customers more than a similar offer in Russia).
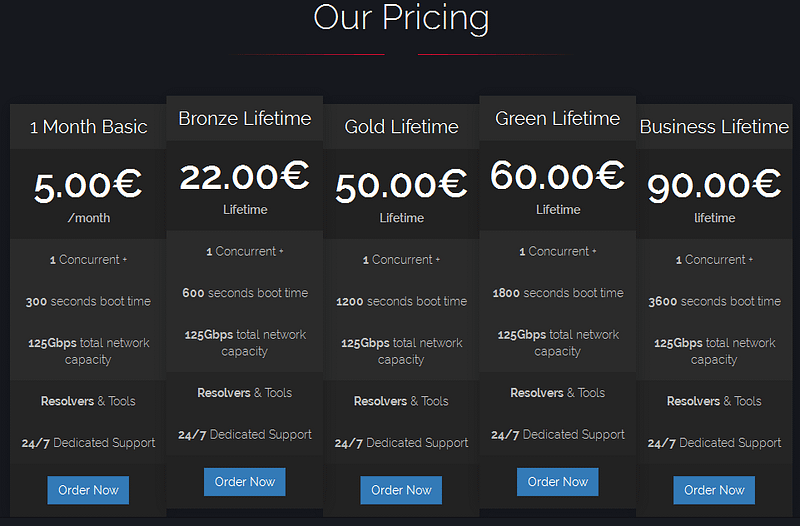
Along with specific botnet features, the organizers of DDoS services also offer customers a tariff plan in which the buyer pays a per-second rental price for botnet capacity. For example, a DDoS attack of 300 seconds using a botnet with a total bandwidth of 125 Gbps will cost €5, with all other characteristics (power and scenarios) remaining the same for all tariffs.
The price list for one of the biggest services offering DDoS attacks
A DDoS attack lasting 10,800 seconds will cost the client $60, or approximately $20 per hour, and the attack specifications (scenario and computing power used) were not always stated on the customer-facing resource. Apparently, not all cybercriminals consider it appropriate to disclose the inner workings of their botnet (it’s also possible that some owners don’t actually understand the technical characteristics of their botnets). In particular, they don’t disclose the type of bots included in a botnet.
The price includes implementation of the following rather trivial scenarios:
- SYN-flood;
- UDP-flood;
- NTP-amplification;
- Multi-vector amplification (several amplification scenarios simultaneously).
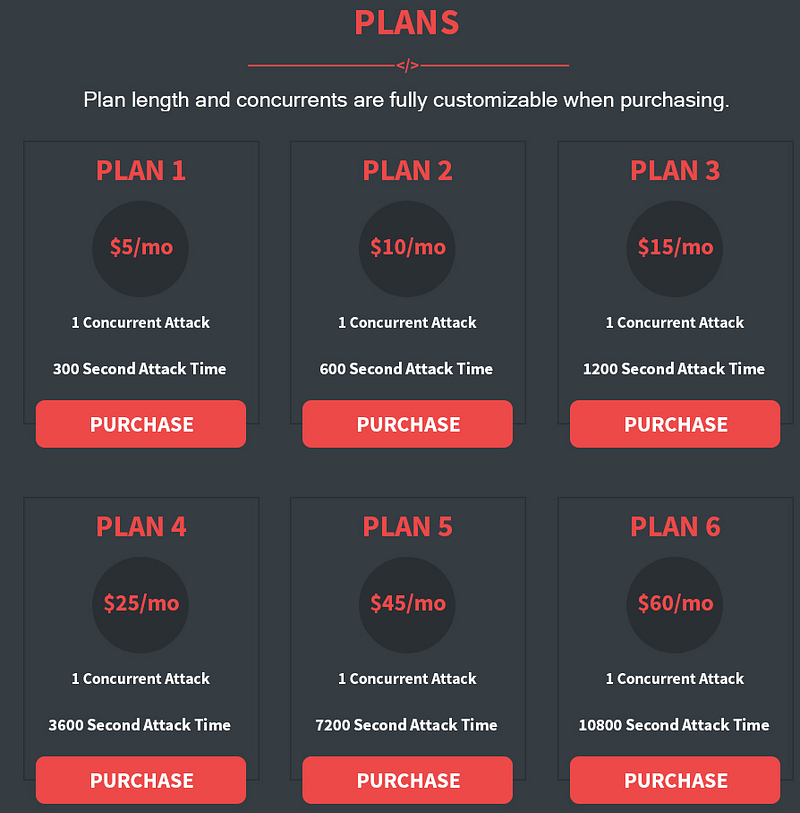
The price list for a service that, with just a few clicks, allows clients to order a DDoS attack on an arbitrary resource accompanied with a detailed report
Some services offer a choice of attack scenario, which allows cybercriminals to combine different scenarios and perform attacks tailored to the individual characteristics of the victim. For example, if the victim successfully combats SYN-flood, the attacker can switch the scenario on the control panel and evaluate the victim’s reaction.
Various tariffs of an English-language service that varies its pricing according to the number of seconds a DDoS attack lasts
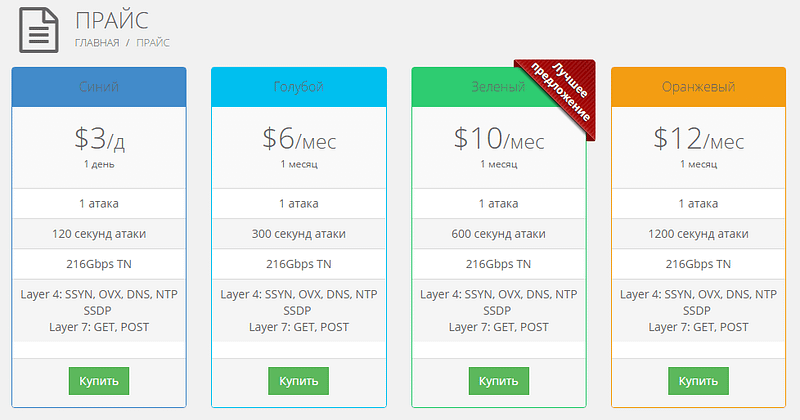
Among the offers we analyzed there were some in which the attackers stated different prices for their services depending on the type of victim.
Information found on a Russian site dedicated entirely to DDoS services
For example, the cybercriminals ask for $400 per day to attack a site/server that uses anti-DDoS protection, which is four times more expensive than an attack on an unprotected site.
Moreover, not all cybercriminals offering DDoS attacks will agree to attack government resources: such sites are closely monitored by law enforcement agencies, and the organizers don’t want to expose their botnets. However, we did come across services offering attacks on government resources as a separate item in the price list.
“The price may change if the resource has political status” reads a resource promoting DDoS attacks
Interestingly, some criminals see nothing wrong with providing protection from DDoS along with their DDoS attack services.
Some services offering DDoS attacks may also offer protection from such attacks
Pricing: a “cloud” example
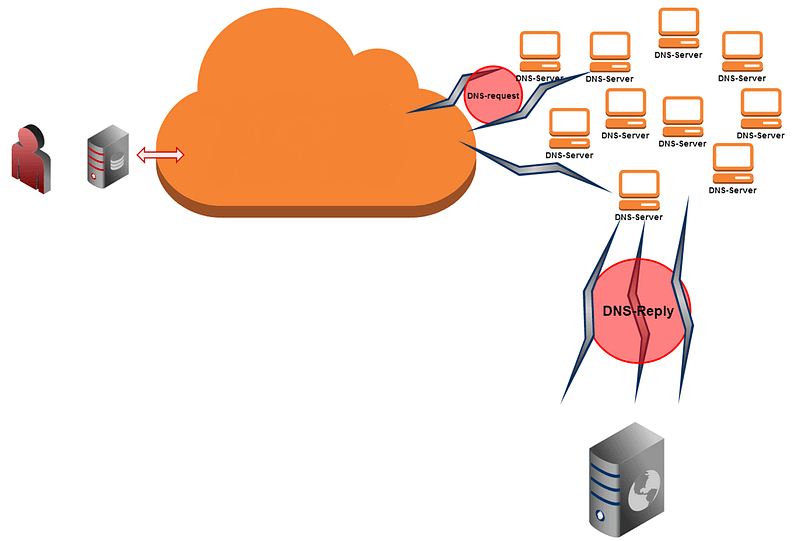
Let’s consider a DNS amplification attack scenario. This type of attack involves the sending of a specially formed request (for example, 100 bytes in volume) to a vulnerable DNS server that responds to the “sender” (i.e. the victim) with a larger volume (kilobyte) of data. The botnet may consist of tens or even hundreds of such servers or the resources of a public cloud service provider. Add in public web load testing services that can be used to carry out a SaaS amplification attack, and we end up with a fairly heavy “sledgehammer”.
DDoS = Cloud + DNS Amplification + SaaS Amplification
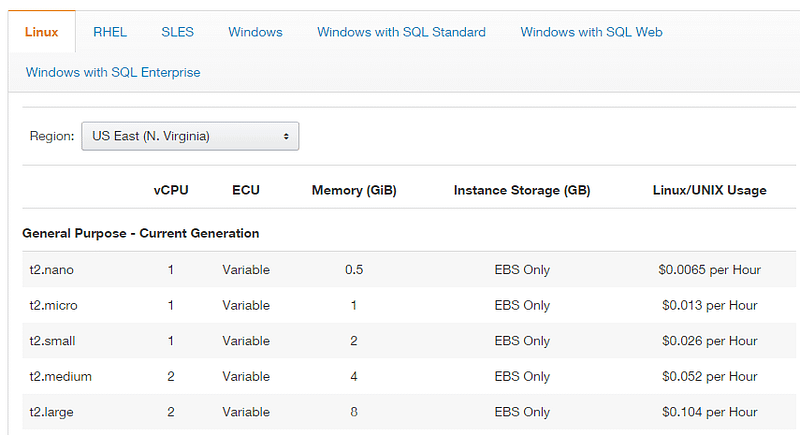
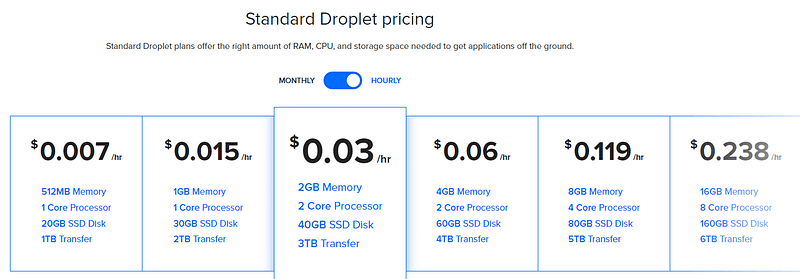
The cost of this service depends on the cost of the provider’s resources. Let’s take Amazon EC2 as an example – the price for a virtual dedicated server with minimal configuration (for a DDoS attack, the configuration of the infected workstation is not as important as its bandwidth connection) is about $0.0065 per hour. Therefore, 50 virtual servers for the organization of a low-powered DDoS attack on an online store will cost cybercriminals $0.325 per hour. Taking into account additional expenses (for example, a SIM card to register an account and adding a credit card to it), an hour-long DDoS attack using a cloud service will cost the criminals about $4.
Price list for popular cloud service providers
This means the actual cost of an attack using a botnet of 1000 workstations can amount to $7 per hour. The asking prices for the services we managed to find were, on average, $25 per hour, meaning the cybercriminals organizing DDoS attack are making a profit of about $18 for every hour of an attack.
Conclusion
The clients of these services understand perfectly well the benefits of DDoS attacks and how effective they can be. The cost of a five-minute attack on a large online store is about $5. The victim, however, can lose far more because potential customers simply cannot place an order. We can only guess how many customers an online store loses if an attack lasts the whole day.
At the same time, cybercriminals continue to actively seek new and cheaper ways to organize botnets. In this regard, the Internet of things makes life easier for them. One of the current trends is the infection of IoT devices (CCTV cameras, DVR-systems, “smart” household appliances, etc.) and their subsequent use in DDoS attacks. And while vulnerable IoT devices exist, cybercriminals are able to exploit them.
It should be noted that DDoS attacks and, in particular, ransomware DDoS have already turned into a high-margin business: the profitability of one attack can exceed 95%. And the fact that the owners of online sites are often willing to pay a ransom without even checking whether the attackers can actually carry out an attack (something that other fraudsters have already picked up on) adds even more fuel to the fire. All the above suggests that the average cost of DDoS attacks in the near future will only fall, while their frequency will increase.