Medical data is slowly but surely migrating from paper mediums to the digital infrastructure of medical institutions. Today, the data is “scattered” across databases, portals, medical equipment, etc. In some cases, the security of the network infrastructure of such organizations is neglected, and resources that process medical information are accessible from outside sources.
Results that had been obtained during research that we discussed in a previous article called for a more detailed analysis of the security problem, but now from within medical institutions (with the consent of their owners, of course). The analysis allowed us to work on mistakes and give a series of recommendations for IT experts who service medical infrastructure.
The article is prepared especially for Securelist.com
Incorrect diagnosis is the first step to a fatal outcome
Providing data security in medicine is an issue that is more serious than it may seem at first glance. The most obvious scenario, which is the theft and reselling of medical data on the black market, does not seem as scary as the possibility of diagnostic data being modified by evildoers. Regardless of the goals of evildoers (extorting money from hospital owners or attacks targeted at specific patients), nothing good comes to patients as a result: after receiving incorrect data, doctors may prescribe the wrong course of treatment. Even if data substitution is detected in time, the normal operation of the medical institution may be disrupted, prompting the need to recheck all of the information stored on compromised equipment.
According to a report by the Centers for Disease Control and Prevention (CDC), the third leading cause of death in the USA comes from medical errors. Establishing a correct diagnosis depends on, aside from the qualification of a patient’s doctor, the correctness of data that is received from medical devices and stored on medical servers. This means that the resources for connected medicine produce an increased attraction for evildoers.
What is connected medicine?
This term refers to a large number of workstations, servers, and dedicated medical equipment that are connected to the network of a medical institution (a simplified model is shown in the figure below).
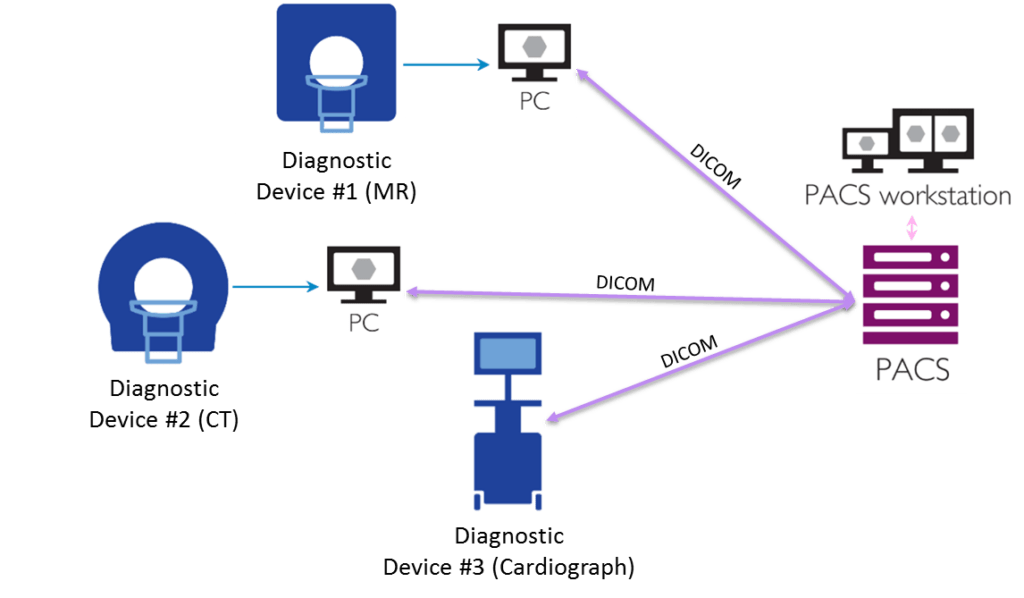
The network topology of connected medicine
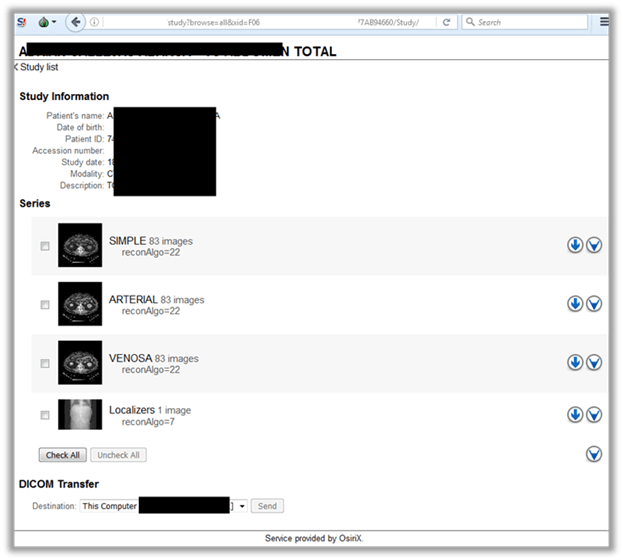
Contemporary diagnostic devices can be connected to the LAN of an organization or to workstations through, for example, USB connections. Medical equipment quite often processes data (for example, a patient’s photographs) in DICOM format, which is an industry standard for images and documents. In order to store them and provide access to them from outside, PACSs (Picture Archiving and Communication Systems) are used, which can also be of interest to evildoers.
Recommendation #1: remove all nodes that process medical data from public access
It should be obvious that medical information should remain exclusively within the LAN of an institution. Currently, however, more than one thousand DICOM devices are in public access, which is confirmed by statistics obtained by using the Shodan search engine.
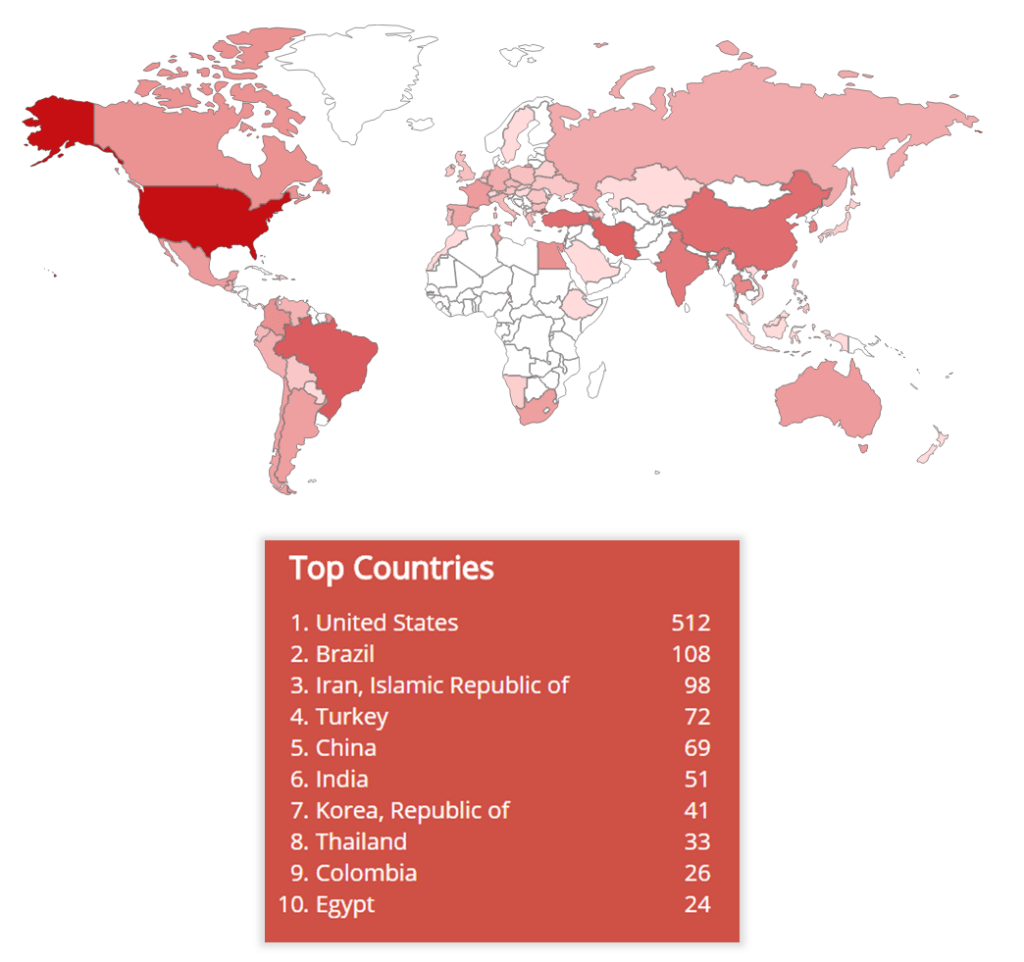
The geographical spread of DICOM devices (according to data from the Shodan search engine)
Generally, all types of PACS servers, which store information valuable to evildoers, are in public access. PACSs should be placed within the corporate perimeter, insulated from unauthorized use by third parties, and periodically backed up.
Recommendation #2: assign counter-intuitive names to resources
Even during the reconnaissance phase, attackers can obtain data that is important for an attack. So, for example, when enumerating available resources, they can find out the names of internal resources (servers and workstations) and thus determine which network nodes are useful to them and which ones are not.
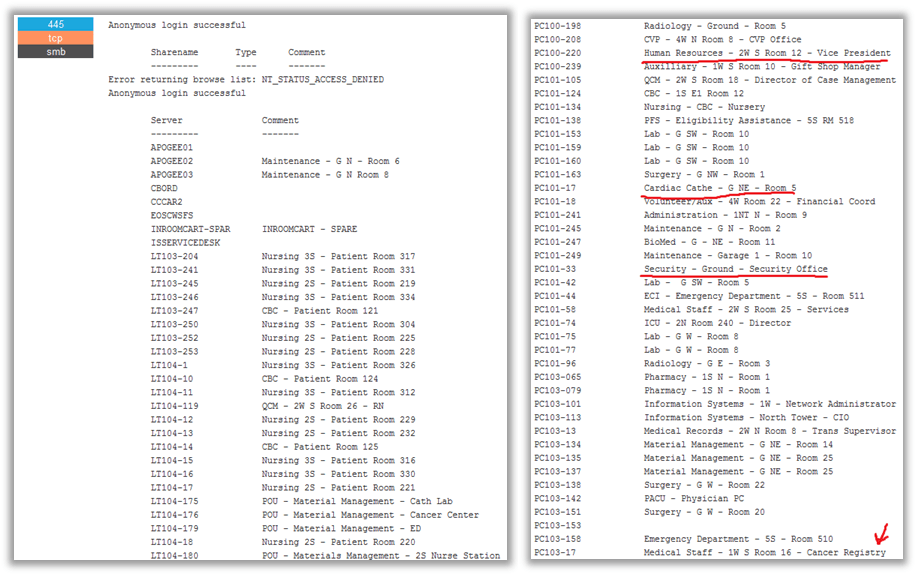
Data about resources on the LAN of an organization that was obtained using open sources
To cite “interesting” resources as an example, let’s note database servers and other locations where medical information is collected. Aside from that, attackers may use obvious resource names to identify workstations with connected medial equipment.

An example of poor naming of internal resources on the LAN of a medical institution, which shows attackers where valuable data is kept
In order to make things harder for evildoers, obvious naming practices should be avoided. There are recommendations out there on how to name workstations and servers that have been compiled by competent organizations. We suggest that you take a look.
Recommendation #3: periodically update your installed software and remove unwanted applications
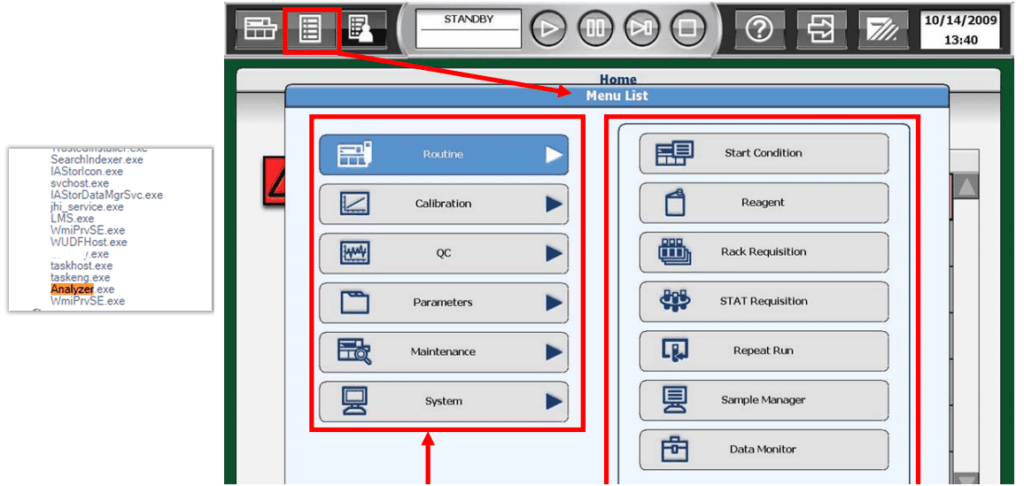
Evildoers may find many potential entry points when analyzing installed software on network nodes that process valuable information. In the example below, a workstation has several applications installed that have nothing to do with medicine (the W32.Mydoom worm and the Half-Life Engine game server). Additionally, that list has a series of applications that have critical vulnerabilities with published exploits.
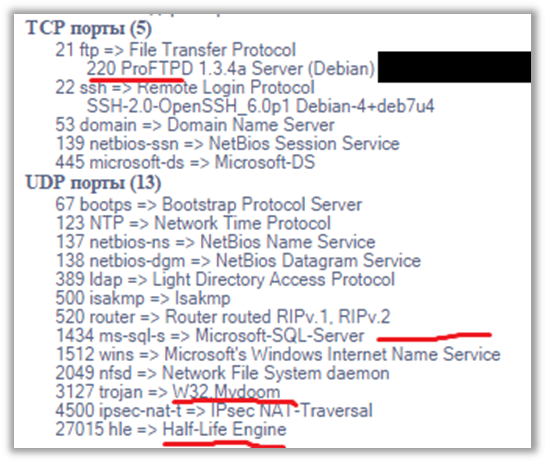
An example of software installed on a workstation with connected medical equipment
One more example of such a careless approach is the installation of third-party software on a server that is responsible for the operation of the institution’s web portal, which allows doctors and patients to remotely access medical data.

A server with a tool for viewing DICOM images that has third-party software as well
In order to rule out the possibility of data access via third-party software, installed applications should be regularly inspected and updated. There should be no extra software on workstations with connected medical equipment.
An example of a vulnerable medical web portal that contains critical vulnerabilities that lead to medical data.
Recommendation #4: refrain from connecting expensive equipment to the main LAN of your organization
Medical devices used to help perform diagnoses and operations are very often expensive in terms of maintenance (for example, calibration), which requires significant financial investments from the owner.
An evildoer who gains access to equipment or a workstation with a connected device may:
-
- exfiltrate medical data directly from the device;
-
- spoof diagnostic information;
- reset equipment settings, which will lead to unreliable data output or temporary incapacitation.
In order to gain access to data that is produced by the device, an evildoer only has to search for specific software.
An evildoer may isolate medical applications on the list of installed software on a workstation and modify operation parameters for medical equipment
To prevent unauthorized access to equipment, it is necessary to isolate all of the medical devices and workstations connected to them as a separate LAN segment and provide a means to carefully monitor events occurring in that segment (see also recommendation #5).
Recommendation #5: provide timely detection of malicious activity on your LAN
When there’s no opportunity to install a security solution directly on the device itself (sometimes warranties prohibit any modifications at the operating system level), alternative options for detecting and/or confounding evildoers should be found. We discussed one of these options in the article titled “Deceive in Order to Detect”.
The defending party may prepare a set of dedicated traps, which consist of LAN nodes that simulate medical equipment. Any unauthorized access to them may serve as a signal that someone has compromised the network and that the IT department of the medical institution should take appropriate action.
There are numerous methods for detecting malicious activity, and there is no sense in listing all of them as recommendations. Every IT department bases its choice of technology, products, and strategies for providing informational security on a large number of factors (the network size, resource priorities, available finances, etc.). Still, it is important to remember the main thing, which is that a lack of protection in medical infrastructure may cost the lives of patients.