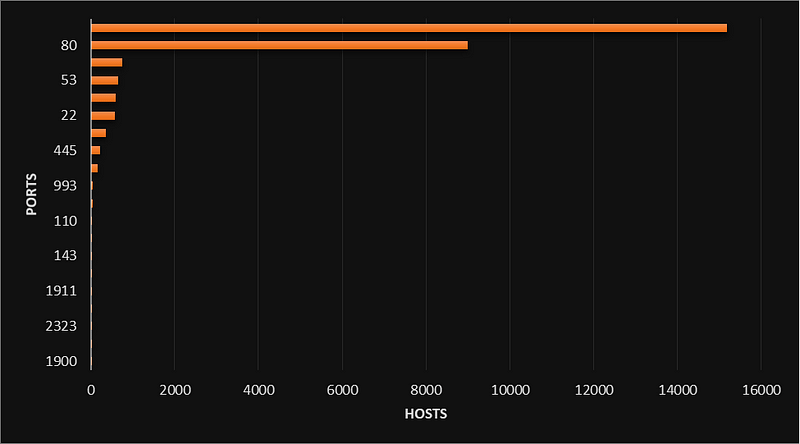
At last year’s Security Analyst Summit 2017 we predicted that medical networks would be a titbit for cybercriminals. Unfortunately, we were right. The numbers of medical data breaches and leaks are increasing. According to public data, this year is no exception.
Blog
Medical data is slowly but surely migrating from paper mediums to the digital infrastructure of medical institutions. Today, the data is “scattered” across databases, portals, medical equipment, etc. In some cases, the security of the network infrastructure of such organizations is neglected, and resources that process medical information are accessible from outside sources.
Медицинские данные медленно, но уверенно мигрируют с бумажных носителей в «цифровую» инфраструктуру медицинских учреждений. Сегодня они «разбросаны» по базам данных, порталам, медицинскому оборудованию и т.п. При этом в некоторых случаях безопасность сетевой инфраструктуры таких организаций остается без внимания, а ресурсы, обрабатывающие медицинскую информацию, доступны извне.
Как показали многочисленные исследования, “умные” дома, “умные” автомобили и “умные” города, не только приносят несомненную пользу человеку в быту, но и зачастую создают угрозу его безопасности. Речь не только об утечке персональных данных – достаточно представить, что в какой-то момент “умный” холодильник под воздействием третьей силы начнет воспринимать просроченные продукты как свежие. Или вот еще один, более печальный сценарий: на высокой скорости система “умного” автомобиля неожиданно для хозяина поворачивает руль вправо…
As numerous studies have shown, smart houses, smart cars, and smart cities are undeniably beneficial to people in everyday life, but quite often can become a threat to their safety. It is not only a matter of personal data leakage. Just imagine that, for example, a smart refrigerator, affected by a third party at one point or another, would begin identifying expired products as fresh. There is yet another more dismal scenario: the system of a smart car turns the vehicle to the right at high speed, catching the driver unaware…