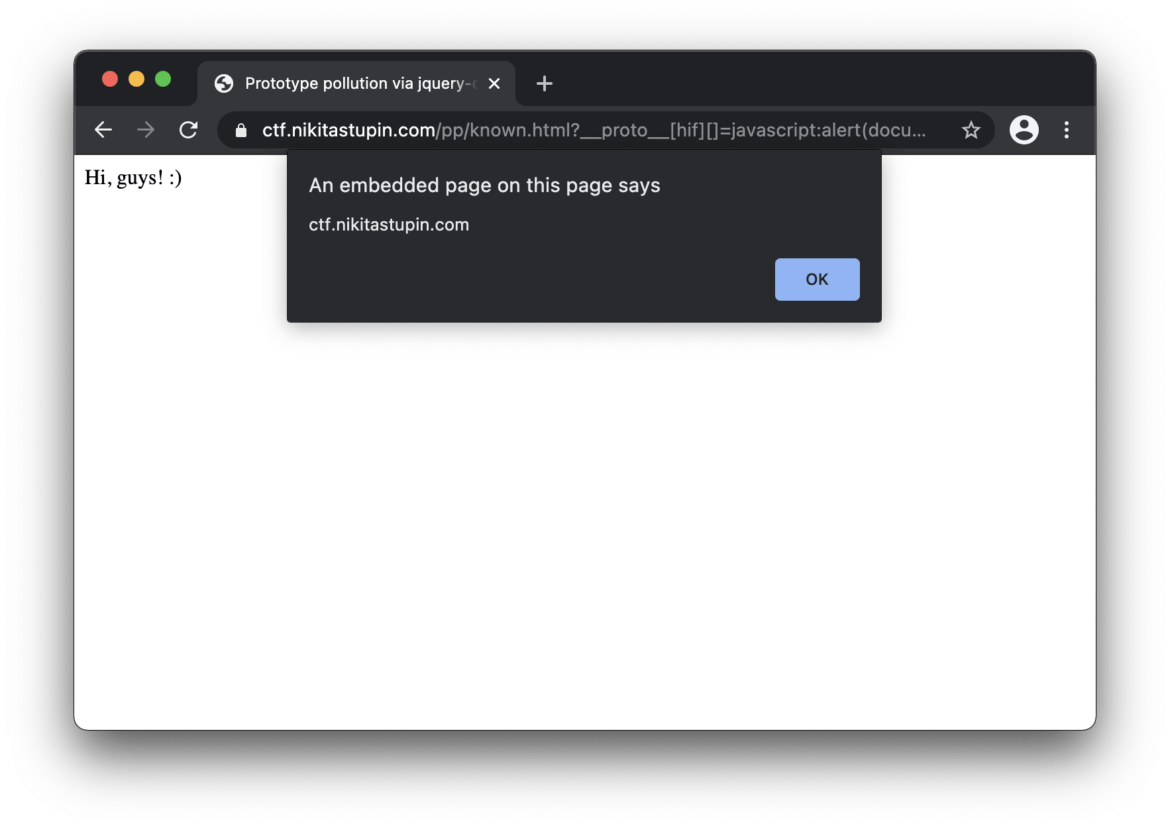
If you regularly monitor bug bounty reports, you’ve seen “JavaScript prototype pollution” titles. Nikita Stupin decided to dig deeper into the category of vulnerabilities, impacting JavaScript applications, and prepared the practical guide of its discovery and exploitation. Soon we will also prepare an English version of the paper, but currently, you have to manage by yourself to translate it.
Denis Makrushin
Denis Makrushin
Denis is chief technology officer of cybersecurity product line at telecommunications company. He is responsible for product development, defining technology strategy and driving future technical innovation.
For everyone who wants to start new year productively and begin the journey in #AppSec, I'll introduce “Web App Bug Hunting: Fundamentals and Learning Path” workshop on #SINCON. Thanks to @dariaski and @Emil0xA for the opportunity. Workshop details: https://t.co/sEpB73RvTh https://t.co/nIoKt2JmCv
— Denis Makrushin (@makrushind) January 2, 2021
For everyone who wants to start the new year productively and begin the journey in application security, I will introduce “Web Applications Bug Hunting: Fundamentals and Learning Path” workshop on SINCON.
Once bug hunting becomes a race of known misconfigurations and CVE detection, automation is required:
- monitor daily #BugBountyTips and CVEs;
- filter results with trendy potential;
- get alerts on time (13:37 UTC +0).
“Bug Hunting Hub” is a Telegram channel with my notes and bot notifications.
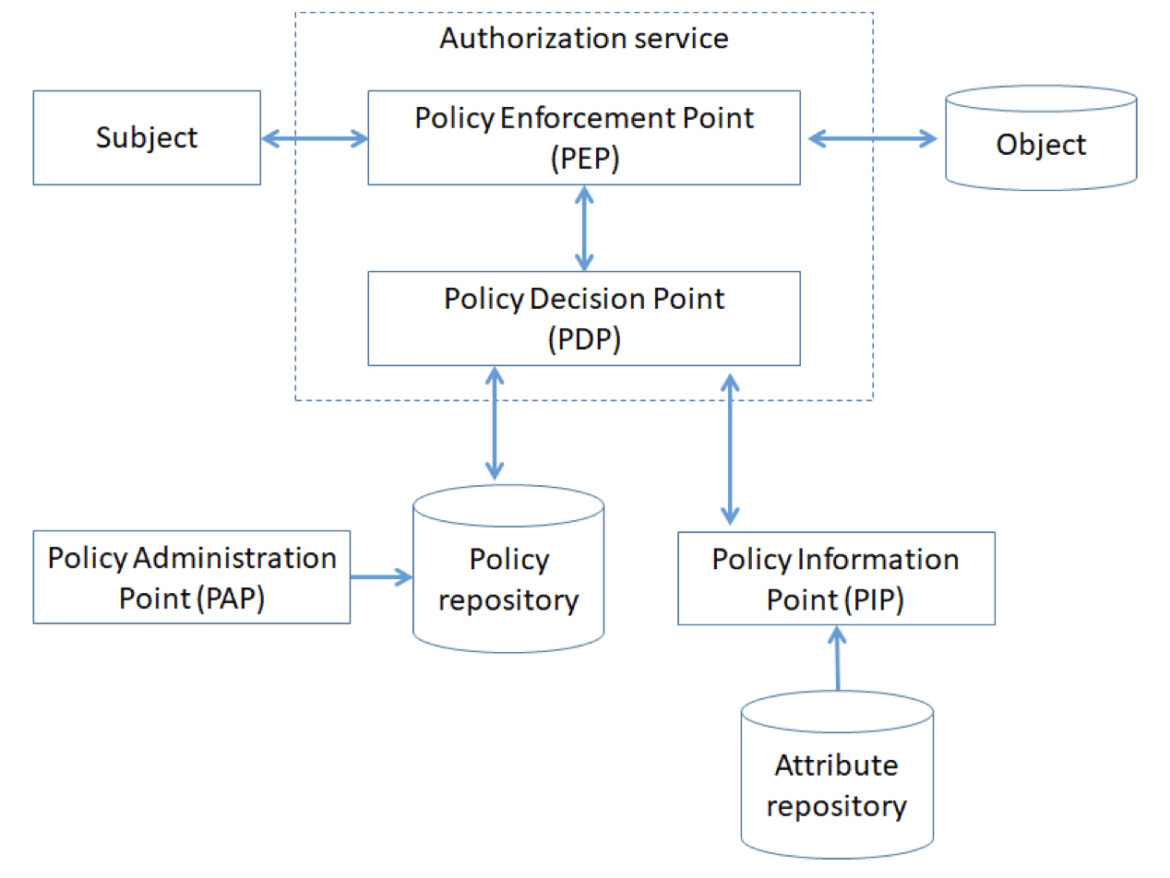
Authentication, Authorization, and Audit (AAA) in microservice-based architecture is a cornerstone for any scale applications. Multiple “best practices” by technology leaders, multiple recommendations by industry influencers. What is relevant to your product design and should be implemented?
We published the survey deliver the AAAnswers with the criteria for choosing the right one for your application security architecture: “Authentication and authorization in microservice-based systems: survey of architecture patterns.”
Objective: the aim of this study is to provide a helpful resource to application security architect and developers on existing architecture patterns to implement authentication and authorization in microservices-based systems.