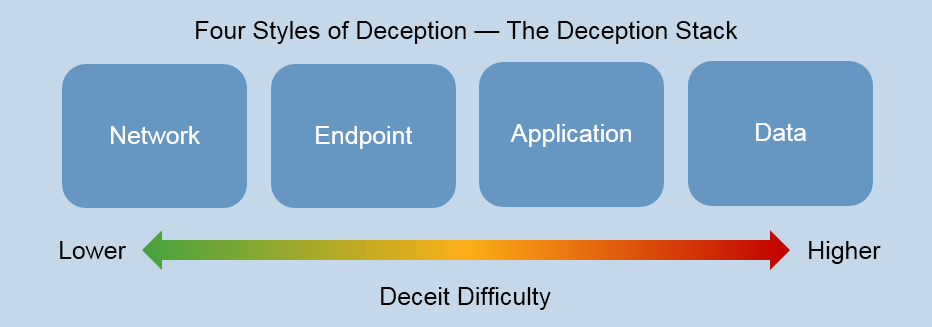
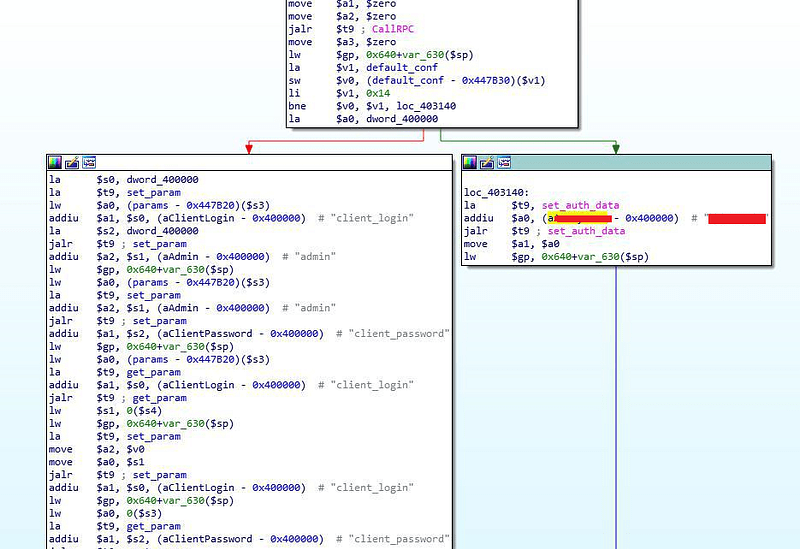
Как бороться с целенаправленными атаками? Очевидно, что нужно какое-то технологическое решение, в котором были бы объединены лучшие идеи по обнаружению неизвестных угроз. Но прежде чем говорить о нем, стоит определиться с тем, что считать целевой атакой, и разобрать, как они работают.
threat intelligence
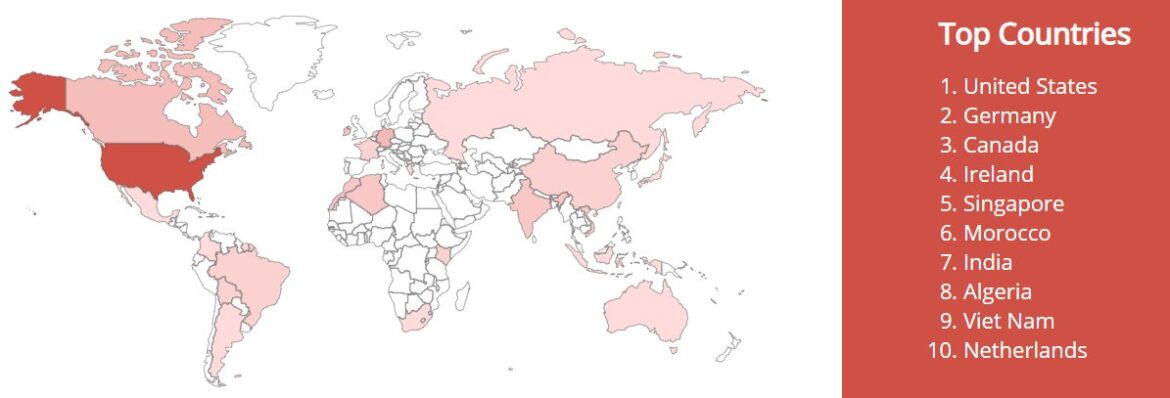
Historically “Indicator of Compromise” appears as a result of compromise. That’s why there is still an illusion that the attacker is one step ahead of his victim. However, the asymmetry can be removed. Classical methods of collecting and processing attributes of an attacker, who has already left his tracks somewhere, can be supplemented and enriched with a new source of IoCs – the Proactive Threat Intelligence.
The latest results of security assessments that have been performed for various medical organizations and vulnerability research of most popular medical web-applications will be presented at
Paper medical records and “medical books” are no longer used in healthcare organizations. The “papers” were replaced by electronic medical records (EMR) containing the entire history of patient’s requests, diagnostic of diseases and treatment procedures. Medical organizations use special software for managing medical procedures and storing patient data.
“If you want to change the world, start with yourself.” In the case of security research this can be rephrased to: “If you want to make the world safer, start with the smart things in your home.” Or, to be more specific, start with your router — the core of any home network as well as an interesting research object. And that router you got from your ISP as part of your internet contract is even more interesting when it comes to research.