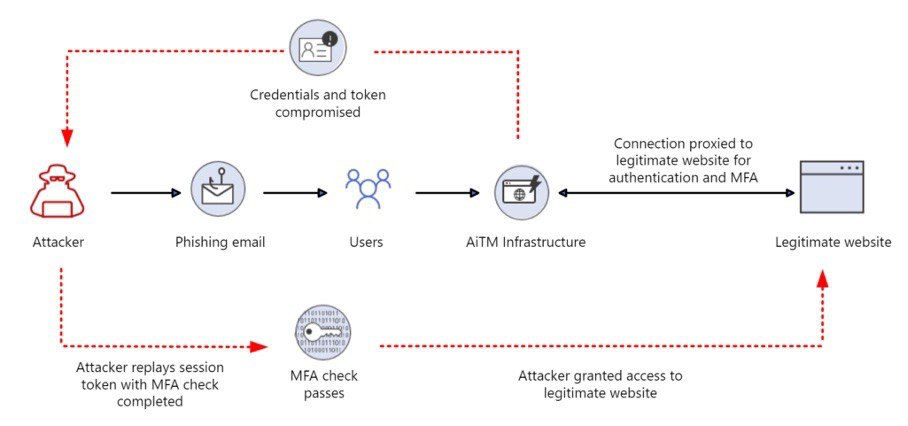
Типичный сценарий социотехнического пентеста: собрал список корпоративных email-адресов, настроил инструмент для проведения фишинговых рассылок, провел рассылку, получил учетные данные сотрудников для доступа в корпоративную инфраструктуру.
threat intelligence
Back in 2015, I had my first international talk at Nullcon in India. Warm community, great people. I left with Indian friends and strong impression.
Five years later, BSides Cairo became my first experience on the other side of the table — joining the Advisory Board.
Now the paths cross again: I’m joining BSides Vizag as an Advisory Board member to help bring best-in-class research to the stage.
CFP is open. Submit your research and let’s make it big.
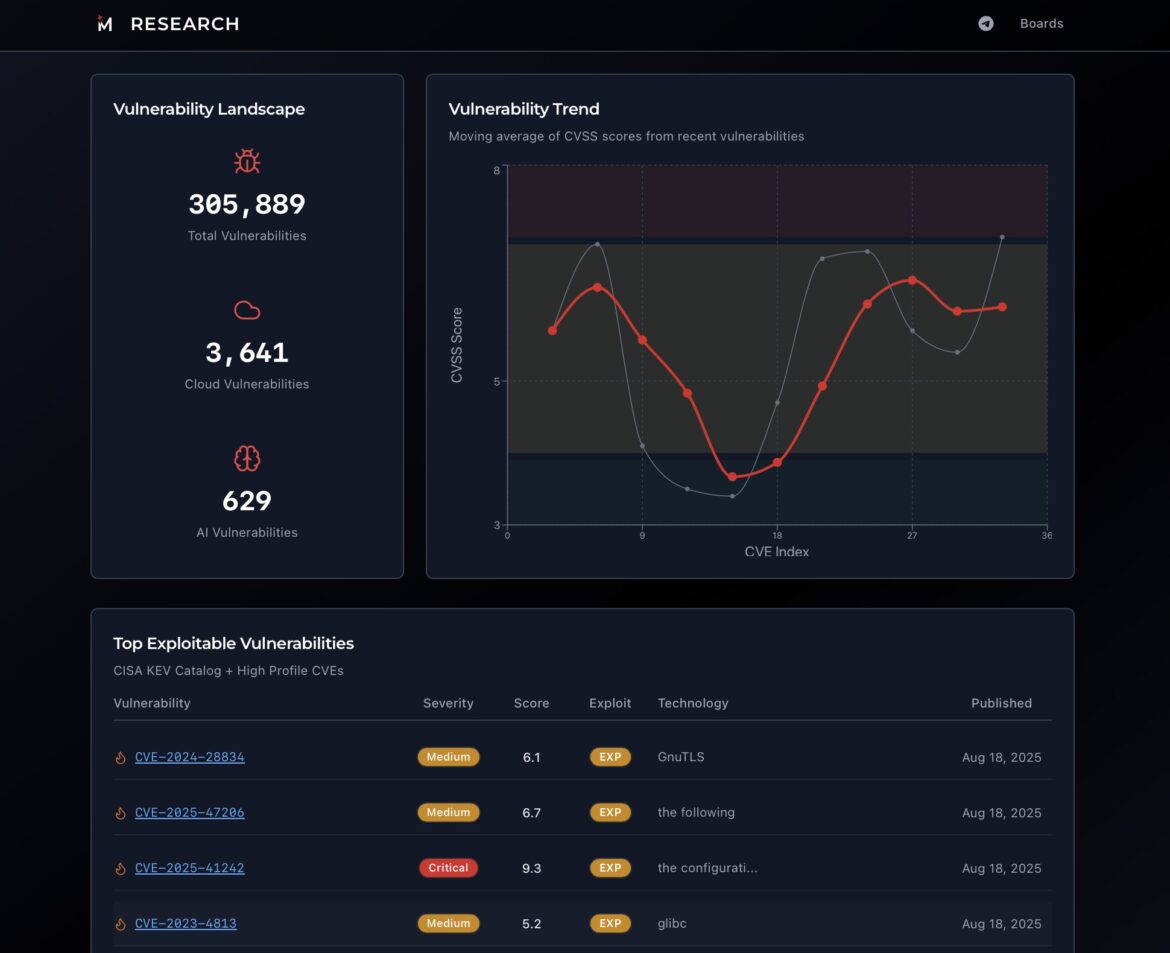
As long as the CVE remains the main index of known vulnerabilities, teams of security analysts and engineers will develop processes to track updates. They will not only track changes, but also enrich database with additional data to help them prioritise fixes accurately.
Back in 2020, when X was still called Twitter, I created a simple Telegram bot that analysed Twitter feeds and identified interesting ideas related to vulnerability detection. Every day, it analysed all the posts with the #bugbountytips hashtag from the previous 24 hours, selected the posts with the highest reach based on the number of likes and retweets, and published them to the feed.
Since then, Twitter has shut down its API and rebranded as X and implemented anti-scraping measures to block content harvesting. However, the number of valuable ideas and the size of security community on the platform have not decreased.
With a bit of vibe-coding, the bot can be brought back to life:
- The bot uses Playwright to collect and analyse content on X with the hashtags #bugbountytips, #bugbountytip, #bugbounty, #pentest and #redteam that have received a certain number of likes within 24 hours.
- The bot transmits these posts for analysis to the DeepSeek-V3 model, which parses each post and prepares an expert commentary.
- It publishes the result in the @bhhub Telegram channel at 13:37 (UTC+0).
Link in comments. If you have any ideas for hashtags or sources to add for monitoring, please share them in the comments or via DM.
Finding secrets in code can be done quickly and accurately if you know their exact format and search within your own project. The task becomes significantly harder when scanning across multiple projects or an enterprise monorepo. The challenge becomes even bigger if the search area is a developer platform and your secret format is nondeterministic.
Effective secret detection and leak prevention during development are crucial for protecting projects from data breaches. The secret-scanning workflows presented here are designed for defensive use in trusted CI/CD pipelines. By combining lightning-fast push-protection scans with deeper, high-precision sweeps of large codebases, this approach enables defenders to find and revoke leaked credentials right at commit time or during routine audits. This gives them an advantage over any adversary scraping the codebase for sensitive data.
This article will walk you through the discovery phase for a secret analyzer. We’ll explore the latest secret scanning tools, understand their constraints, and identify ways to improve three key metrics of secret scanning: precision, recall, and speed.