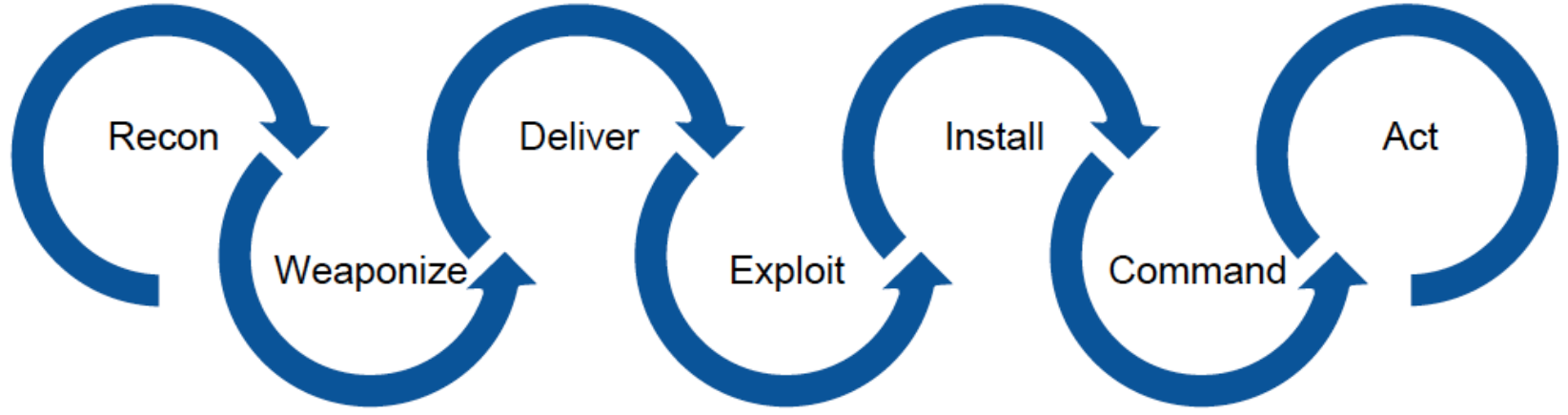
What can we do to eliminate the risk of the targeted attacks? Obviously, we need to implement some kind of technical solution, which would combine the best ideas in the field of unknown threats detection. However, before talking about the solution, let’s try to understand the nature and the meaning of the “targeted attack,” as well as key principles of an offensive operation.
