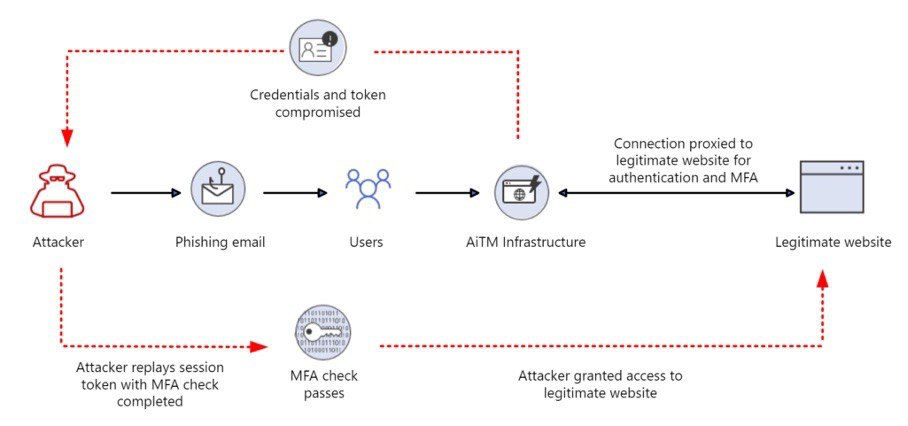
Типичный сценарий социотехнического пентеста: собрал список корпоративных email-адресов, настроил инструмент для проведения фишинговых рассылок, провел рассылку, получил учетные данные сотрудников для доступа в корпоративную инфраструктуру.
Blog
After completing the MBA programme, I had opportunity to spend additional semester focusing on advanced management disciplines and preparing my master’s thesis. This stage was primarily dedicated to research, with many ideas grounded in academic papers.
Back in 2015, I had my first international talk at Nullcon in India. Warm community, great people. I left with Indian friends and strong impression.
Five years later, BSides Cairo became my first experience on the other side of the table — joining the Advisory Board.
Now the paths cross again: I’m joining BSides Vizag as an Advisory Board member to help bring best-in-class research to the stage.
CFP is open. Submit your research and let’s make it big.
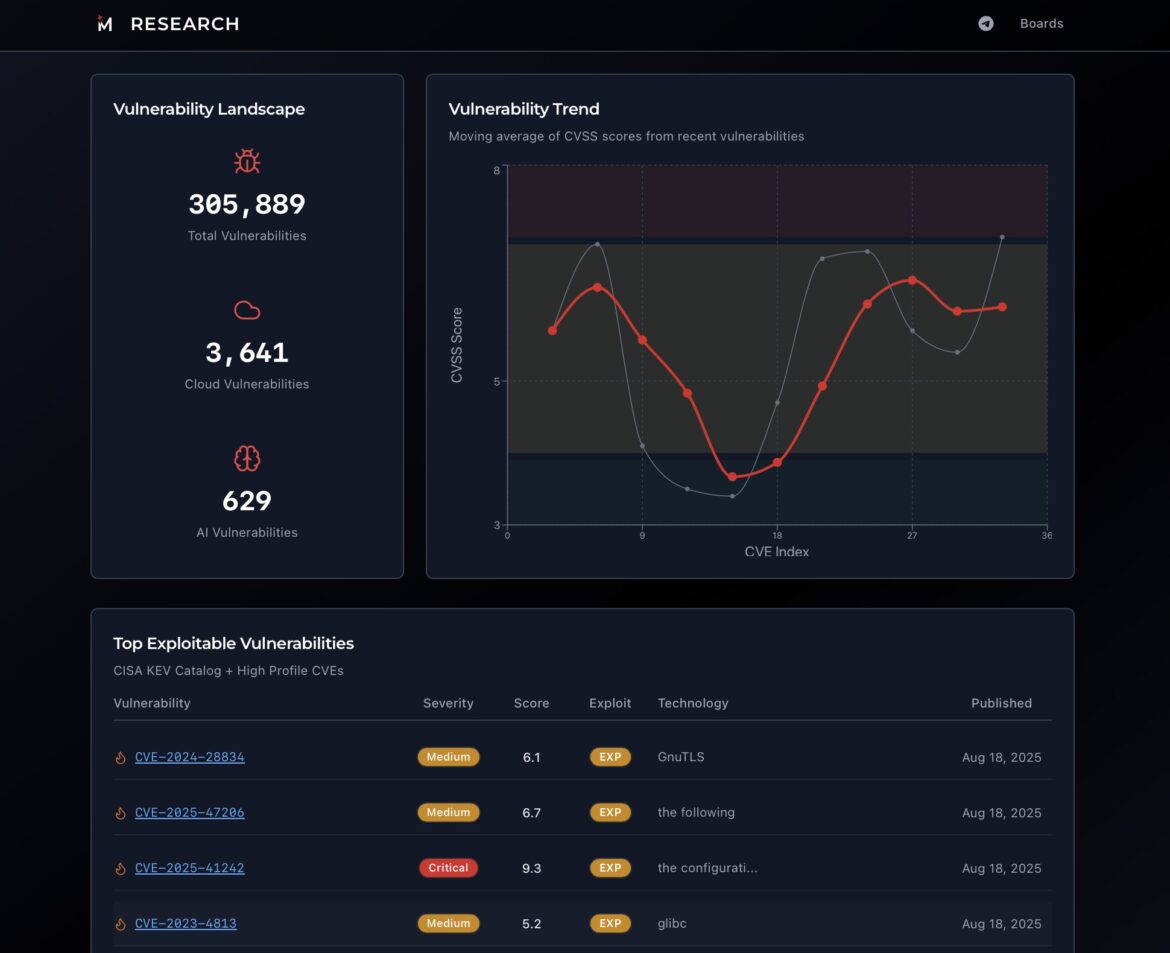
As long as the CVE remains the main index of known vulnerabilities, teams of security analysts and engineers will develop processes to track updates. They will not only track changes, but also enrich database with additional data to help them prioritise fixes accurately.
At the heart of our AppSec platform is an open-source project called Trivy. It’s a software composition analysis tool that helps developers to detect issues in dependencies used in their code.
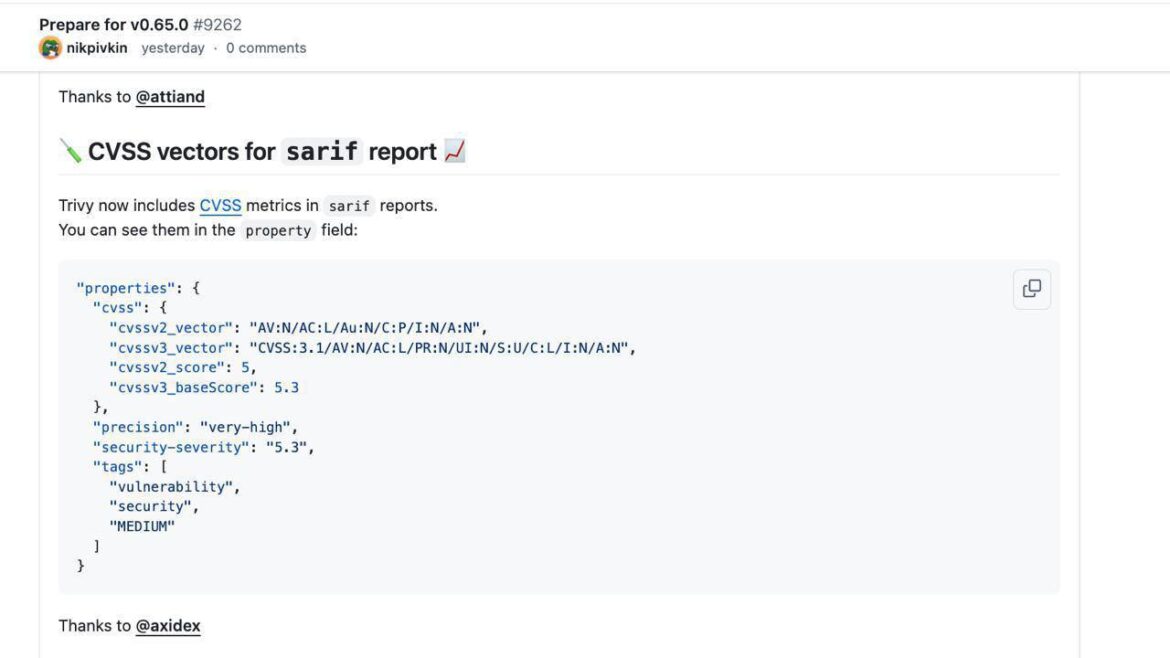
This time, we are not only integrating, but also contributing: in Trivy 0.65.0 release, our developer, Stepan Dolgintsev, added the CVSS vector support. This means that CVSS itself will soon appear on our Supply Chain page, enabling developers and AppSec engineers to triage vulnerabilities more accurately.
The Trivy team has acknowledged this contribution. Congratulations to Stepan on taking his first steps in the world of large open-source projects! Thanks also to Andrey Kuleshov for idea to propose the update to project maintainers.