To properly implement a product maturity program, organizations need to embed and grow security expertise. Cultivation of application security champions requires the right pivot point in the following topic: application bug hunting and mitigation strategy.
Denis Makrushin
Denis Makrushin
Denis is chief technology officer of cybersecurity product line at telecommunications company. He is responsible for product development, defining technology strategy and driving future technical innovation.
We discovered two more JS Prototype Pollution vulnerabilities in one more nmp-package: CVE-2020-28449, CVE-2020-28450. The package has ~200 weekly downloads, so the popularity level is limited. However, due to the patch is still unavailable check the details and make sure that your Node.js app is not affected.

Quick summary of Bug Hunting Village, the first time we organized offline:
- 12 talks and workshops focused on vulnerability research and bug bounty;
- highest payouts during two days of conference by our partners (thanks to Mail.ru Group, VK.com, Азбука Вкуса, Avito, iSimpleLab);
- prizes for most active bug hunters (thanks to PHDays organizers and Timur Yunusov);
- communication in our Chat and knowledge sharing in Telegram-channel, and continuous movement to the next offline event.
Organised within a separate section at PHDays for the first time, leading security researchers and bug hunters will share the results of their work, and owners of bug bounty programs can attract bug hunters by making an announcement. During the event, our sponsors and partners will announce the highest bounties for their vulnerability disclosure programs, and the most active bug hunters will be additionally awarded by organisers.
Submit your talk, workshop or just register yourself to participate here (for Russian-based submissions).
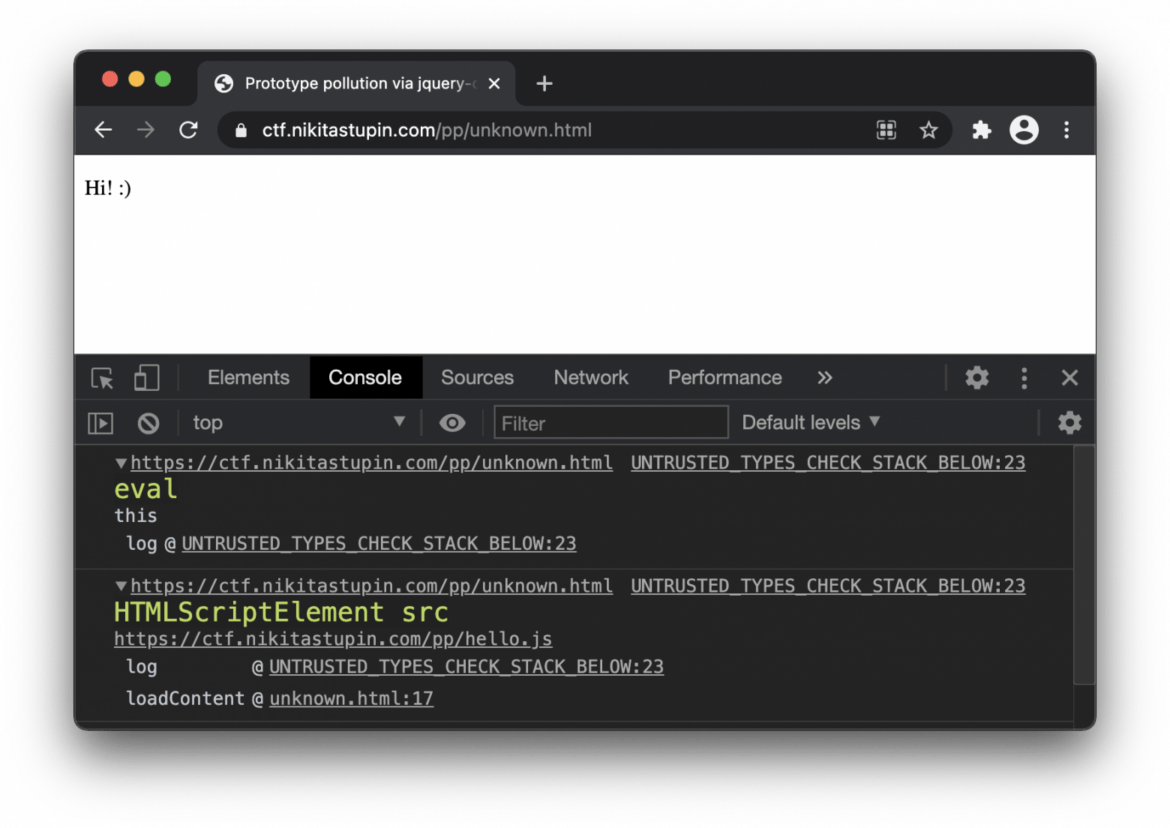
Finally, the English version of “JavaScript prototype pollution: practice of finding and exploitation” article is prepared. Using the techniques Nikita Stupin discovered CVE-2020–28460 in multi-ini parser and a vulnerability in the merge-deep package. With the first one, everything went smoothly, but with the second one, a funny situation came out: after sending the report, the maintainer did not get in touch for a long time, and as a result, GitHub Security Lab found the same vulnerability, managed to reach the maintainer earlier and registered it (GHSL-2020–160). All details related to these vulnerabilities, discovery and exploitation techniques, and recommendations on how to protect your applications are collected in the article.